Safeguarding Digital Privacy: Key Strategies and Tools
Introduction:
In an age where data is the new currency, privacy preservation is not just a preference but a necessity. The article discusses the privacy aspects of cybersecurity, emphasizing the importance of protecting personal and corporate data from unauthorized access and exposure.
Cyber Sales Advisor GPT
https://chat.openai.com/g/g-LlTzr1MId-cyber-sales-advisor/
Fundamental Privacy Concepts:
- Data Minimization: Collect only what is necessary.
- Consent and Choice: Ensuring user consent is paramount.
- Access Control: Limiting data access to authorized personnel.
Encryption Technologies:
- End-to-End Encryption: Protects data in transit, making it accessible only to the communicating users.
- Disk Encryption: Full disk encryption tools like LUKS and VeraCrypt secure data at rest.
Anonymity Tools:
- Tor: Provides anonymous web browsing to protect user identity.
- VPN Services: Masks IP addresses and encrypts internet traffic, enhancing user privacy.
Secure Communication Platforms:
- Signal: A messaging app offering encrypted voice and text communication.
- ProtonMail: An email service that provides encrypted email capabilities.
Privacy-Enhancing Technologies (PETs):
- Zero-Knowledge Proofs: Allows one party to prove to another that a statement is true without revealing any information beyond the validity of the statement itself.
- Differential Privacy: A system for publicly sharing information about a dataset by describing the patterns of groups within the dataset while withholding information about individuals in the dataset.
Privacy Regulations and Compliance:
- GDPR: Outlines the rights of EU citizens regarding data privacy and the obligations of organizations to protect these rights.
- CCPA: Grants California residents new rights regarding their personal data and aims to provide transparency and control over personal information.
Challenges and Considerations:
- Balancing Security and Privacy: Finding the right tools that provide robust security without infringing on user privacy.
- Staying Up-to-Date: Keeping abreast of new regulations and technological advancements.
Cybersecurity Sales Assistant Chatbot

Conclusion:
Privacy is a critical component of a comprehensive cybersecurity strategy. By employing a combination of encryption, anonymization tools, secure communication platforms, and adhering to privacy regulations, organizations can protect themselves and their clients from privacy breaches.
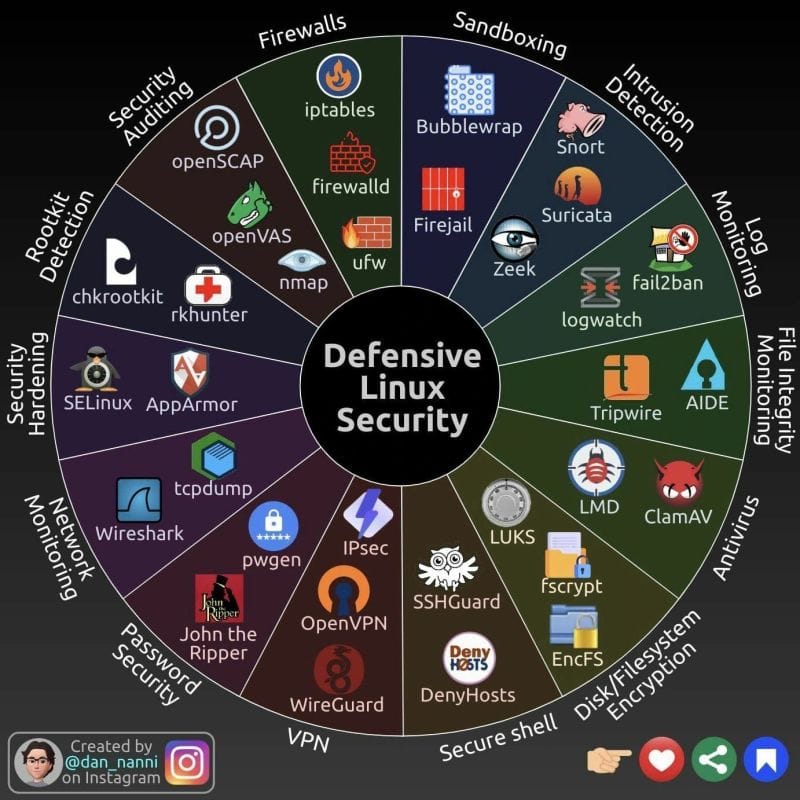
Appendix A - Additional Categories
To enhance this comprehensive diagram of defensive Linux security tools, I'd consider adding a few more categories and tools:
- Container Security:
- Docker Security Scanning
- Clair (vulnerability scanner for containers)
- Falco (runtime security)
- Endpoint Detection and Response (EDR):
- OSSEC (Open Source HIDS)
- Wazuh (enhanced fork of OSSEC)
- Network Access Control:
- FreeRADIUS
- Vulnerability Management:
- OpenVAS (already mentioned, but could be in its own category)
- Nessus (if including non-free options)
- Security Information and Event Management (SIEM):
- ELK Stack (Elasticsearch, Logstash, Kibana)
- Graylog
- Penetration Testing Tools:
- Metasploit Framework
- Burp Suite Community Edition
- Compliance and Auditing:
- Lynis (security auditing tool)
- Data Loss Prevention:
- OpenDLP
- Backup and Recovery:
- Bacula
- Duplicity
- Identity and Access Management:
- FreeIPA
- Keycloak
- Threat Intelligence:
- MISP (Malware Information Sharing Platform)
- Application Security:
- ModSecurity (Web Application Firewall)
- OWASP ZAP (web app scanner)
Adding these categories and tools would provide a more complete picture of the Linux security landscape, covering additional aspects like container security, endpoint detection, and threat intelligence. It would also emphasize the importance of proactive measures like vulnerability management and penetration testing alongside defensive tools.






