The Complete Guide to Aviation Privacy Protection: Secure Your Private Aircraft Operations in 2025
Private aviation represents the ultimate in travel convenience and luxury, offering unprecedented freedom from commercial airline schedules, security lines, and public exposure. Yet this freedom comes with a hidden cost that most aircraft owners and operators never fully understand: comprehensive surveillance of your travel patterns, business relationships, and personal activities through mandatory aircraft tracking systems that broadcast your movements in real-time to anyone with basic monitoring equipment.
Modern aircraft are required to broadcast their location, altitude, speed, and identification information through Automatic Dependent Surveillance-Broadcast (ADS-B) systems that create a detailed digital trail of every flight. This information is collected by government agencies, commercial tracking services, and amateur enthusiasts who publish flight data online, creating unprecedented transparency into the travel patterns of anyone using private aviation.
The implications extend far beyond simple location tracking. Flight data reveals business relationships through travel coordination, family connections through passenger manifests, financial status through aircraft ownership, and operational patterns that can be exploited by criminals, competitors, or anyone seeking to gather intelligence about high-net-worth individuals and their activities.
This comprehensive guide provides specialized privacy strategies designed specifically for aircraft owners, operators, and flight departments who must balance regulatory compliance with operational security and personal privacy. Whether you own a single aircraft or manage a corporate flight department, these evidence-based techniques will help you minimize surveillance exposure while maintaining the freedom and efficiency that makes private aviation valuable.
Understanding the Aviation Privacy Threat Landscape
Private aircraft operations create unique privacy challenges that extend far beyond the aircraft itself. Modern aviation privacy threats encompass multiple interconnected systems including aircraft tracking, ground operations, digital communications, travel coordination, and vendor relationships that collectively create comprehensive surveillance opportunities for anyone seeking intelligence about your activities.
The Aviation Privacy Paradox: Regulatory requirements mandate that aircraft broadcast their location and identification information for safety and air traffic control purposes, directly conflicting with the privacy and security needs of passengers who choose private aviation specifically to avoid public exposure and maintain operational discretion.
Modern aviation threats target high-value individuals and organizations through sophisticated intelligence gathering that combines publicly available flight tracking data with advanced OSINT techniques to build comprehensive profiles of travel patterns, business relationships, and operational vulnerabilities.
Assess your aviation privacy vulnerabilities with our specialized Private Aircraft Cybersecurity & Privacy Assessment. This comprehensive evaluation analyzes your aircraft operations across critical cybersecurity and privacy domains, providing personalized recommendations for aircraft owners, operators, and flight departments concerned with protecting sensitive information and ensuring operational integrity.
The Six Critical Aviation Privacy Risk Categories
Our analysis of aviation privacy incidents and cybersecurity threats reveals that comprehensive protection requires addressing vulnerabilities across six interconnected operational domains:
Technical Systems Security:
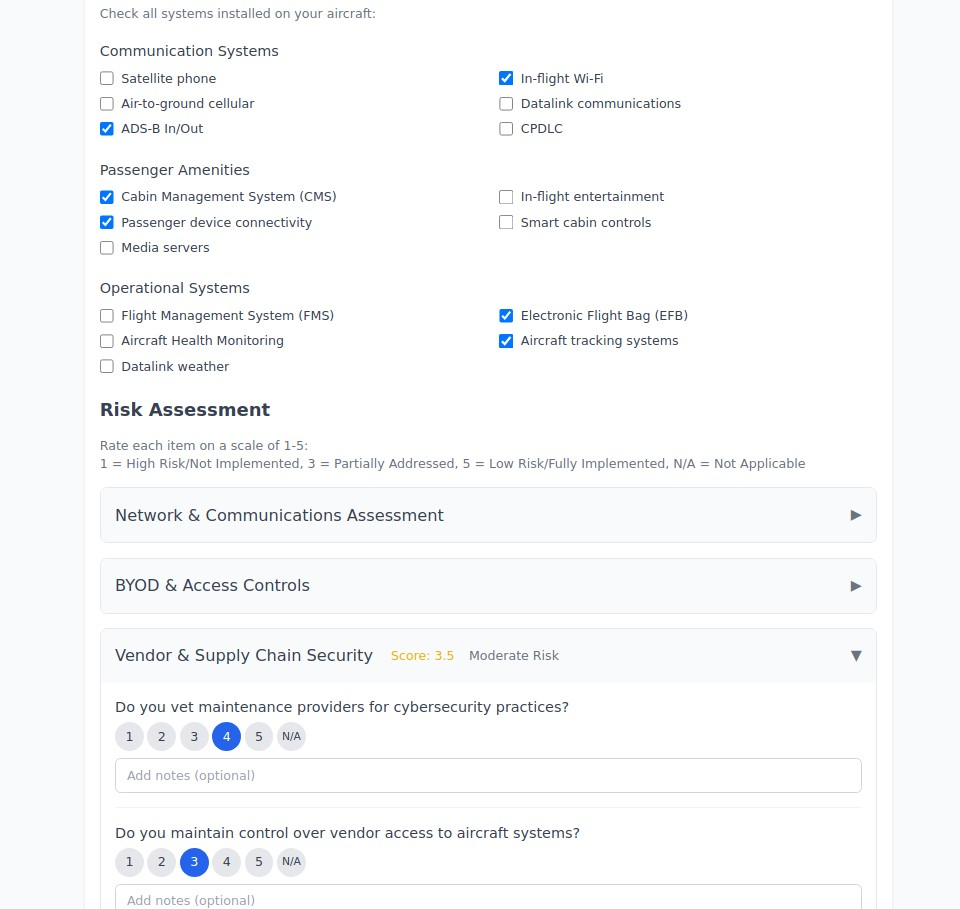
- Aircraft Systems - Avionics, cabin management, communications, and entertainment systems that create potential cybersecurity and privacy vulnerabilities
- Ground Operations - FBO services, maintenance facilities, and hangar operations where physical access to aircraft and systems occurs
Information and Intelligence Exposure:
- Digital Footprint - Aircraft tracking data, flight plans, and crew/passenger information that creates intelligence gathering opportunities
- Travel Chain - Ground transportation, accommodations, and other services that can introduce additional security and privacy risks
Threat Environment Management:
- Vendor & Supply Chain Security - Third-party service providers and maintenance organizations that require access to aircraft systems and operational information
- Threat Environment - Recognition that private aircraft are high-value targets for various threat actors, from cyber criminals seeking financial gain to activists targeting high-profile individuals for tracking or exposure
Each domain represents a different attack surface where aviation privacy can be compromised. Weakness in any area can undermine your entire operational security strategy, while comprehensive protection across all domains creates defense in depth that protects against even sophisticated targeting campaigns.
ADS-B Tracking and Real-Time Surveillance Threats
Automatic Dependent Surveillance-Broadcast (ADS-B) represents the most significant privacy challenge facing private aviation. This mandatory system requires aircraft to continuously broadcast their precise location, altitude, speed, direction, and unique identification code, creating real-time tracking capabilities that anyone with basic equipment can monitor.






