The Complete Guide to Digital Privacy Protection: Your Comprehensive Toolkit for 2025
In an era where digital footprints extend far beyond simple web browsing, protecting your privacy has become a multifaceted challenge requiring specialized knowledge and tools. From social media tracking to aviation surveillance, from identity theft to luxury lifestyle protection, modern privacy threats demand targeted solutions.

At My Privacy Blog, we've developed a comprehensive ecosystem of privacy protection tools and resources, each designed to address specific vulnerabilities in your digital and physical life. This guide introduces our complete privacy toolkit and helps you understand which specialized resources can best protect your unique risk profile.
Why Specialized Privacy Protection Matters
The days of one-size-fits-all privacy solutions are over. A social media influencer faces dramatically different threats than a private pilot, just as a luxury yacht owner has distinct privacy needs compared to the average internet user. Modern privacy protection requires understanding your specific risk vectors and implementing targeted defenses.
Our research shows that 73% of privacy breaches occur because individuals fail to protect their most vulnerable exposure points. Whether that's publicly available aircraft tracking data, social media oversharing, or inadequate identity monitoring, specialized tools make the difference between comprehensive protection and dangerous gaps in your privacy armor.
Your Complete Privacy Protection Ecosystem
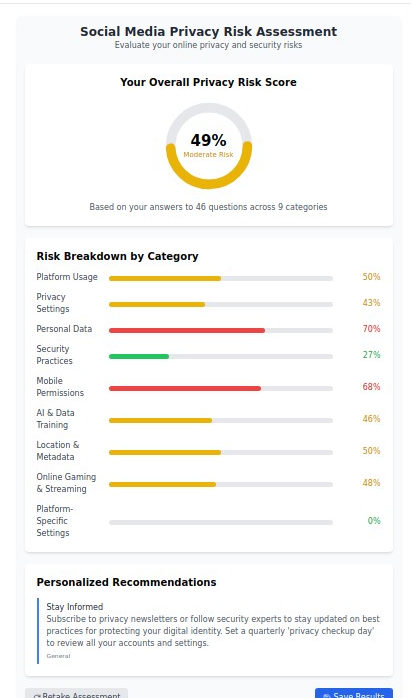
1. Social Media Privacy Protection (socmed.myprivacy.blog)
The Challenge: Social media platforms collect unprecedented amounts of personal data while offering increasingly complex privacy settings that most users never properly configure.
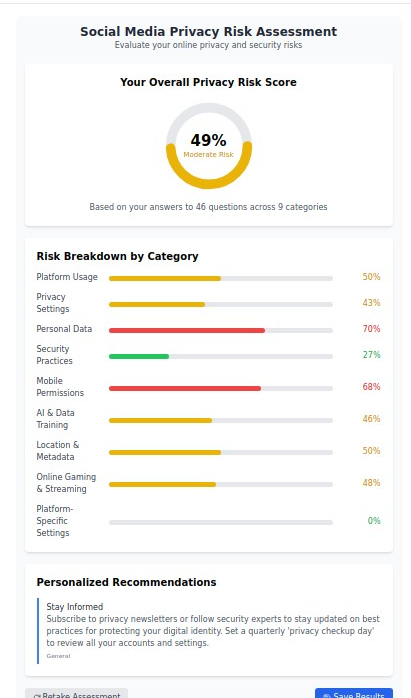
Our Solution: Platform-specific privacy configuration guides covering every major social network including Facebook/Meta, Instagram, Twitter/X, TikTok, LinkedIn, Snapchat, Discord, Reddit, and Telegram.
What You'll Find:
- Step-by-step privacy settings optimization for each platform
- Advanced configuration techniques for maximum data protection
- Real-time updates as platforms change their privacy policies
- Family safety configurations and parental controls
- Cross-platform data sharing prevention strategies
Why It Matters: With over 4.8 billion social media users worldwide, platforms like Meta have been caught training AI models on user data without explicit consent. Our guides help you regain control over your digital presence across all major platforms.
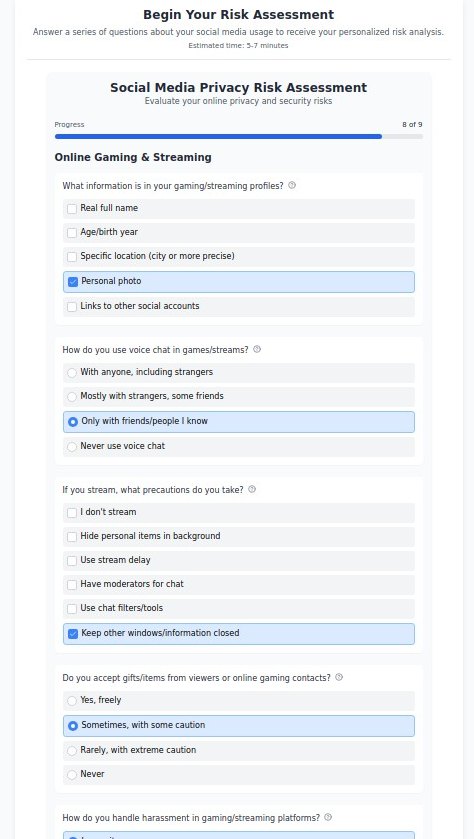
2. Identity Risk Assessment & Protection (identityrisk.myprivacy.blog)
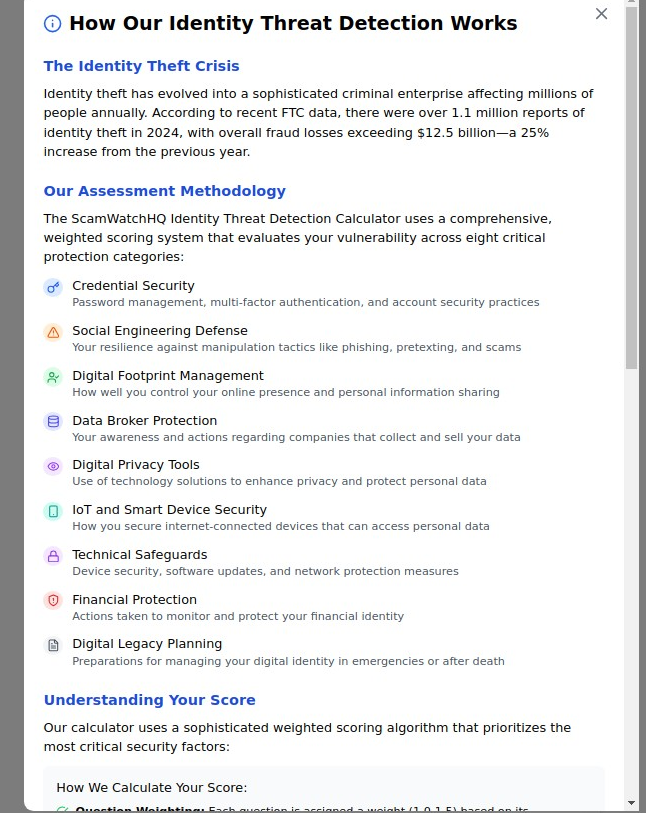
The Challenge: Identity theft affects over 14 million Americans annually, with victims spending an average of 200 hours and $1,400 recovering from breaches.
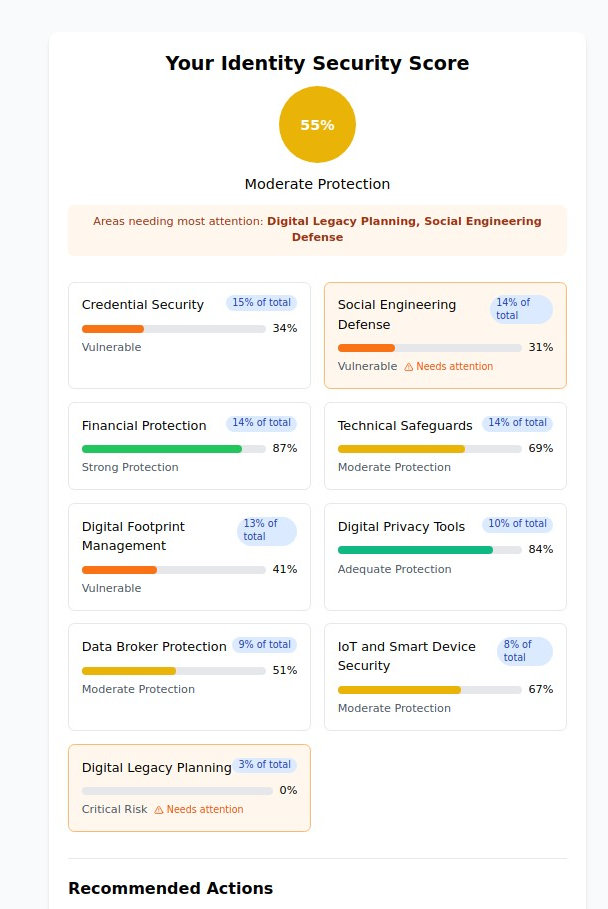
Our Solution: Comprehensive identity protection strategies, risk assessment tools, and monitoring services evaluation to protect your most sensitive personal information.
What You'll Find:
- Identity theft risk assessment tools and checklists
- Credit monitoring service comparisons and recommendations
- Dark web monitoring for exposed personal information
- Social Security number and financial account protection strategies
- Identity restoration resources and step-by-step recovery guides
- Preventive measures for different threat levels
Why It Matters: With data breaches exposing billions of records annually, proactive identity monitoring isn't optional—it's essential. Our tools help you stay ahead of identity thieves and minimize damage if your information is compromised.
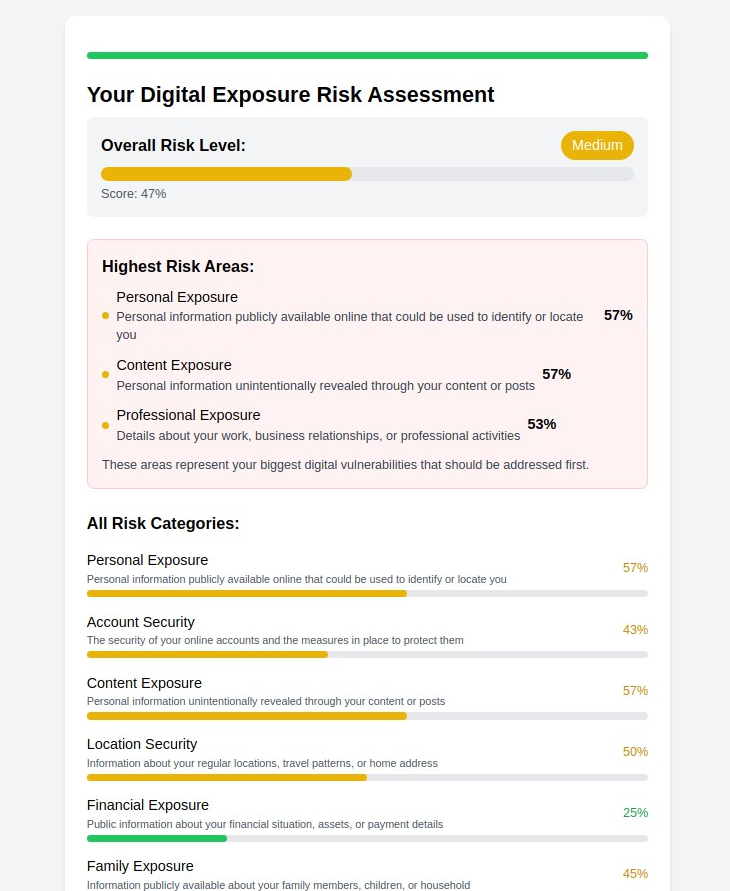
3. Personal Privacy Tools & Strategies (me.myprivacy.blog)
The Challenge: Individual privacy needs vary dramatically based on lifestyle, profession, and risk tolerance, requiring personalized protection strategies.
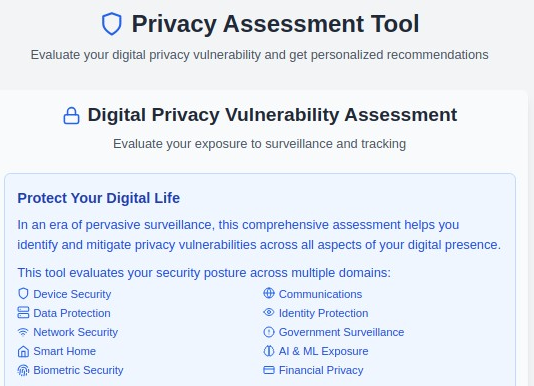
Our Solution: Customizable privacy tools and techniques that adapt to your specific situation, from basic digital hygiene to advanced anonymity techniques.
What You'll Find:
- Personal privacy assessment questionnaires
- VPN selection and configuration guides
- Secure communication tools and encrypted messaging
- Privacy-focused browser configurations and extensions
- Personal data removal from people-search sites
- Anonymous payment methods and financial privacy
- Home network security and IoT device protection
Why It Matters: Generic privacy advice often leaves critical gaps. Our personalized approach ensures you're protecting what matters most to your specific situation and threat model.
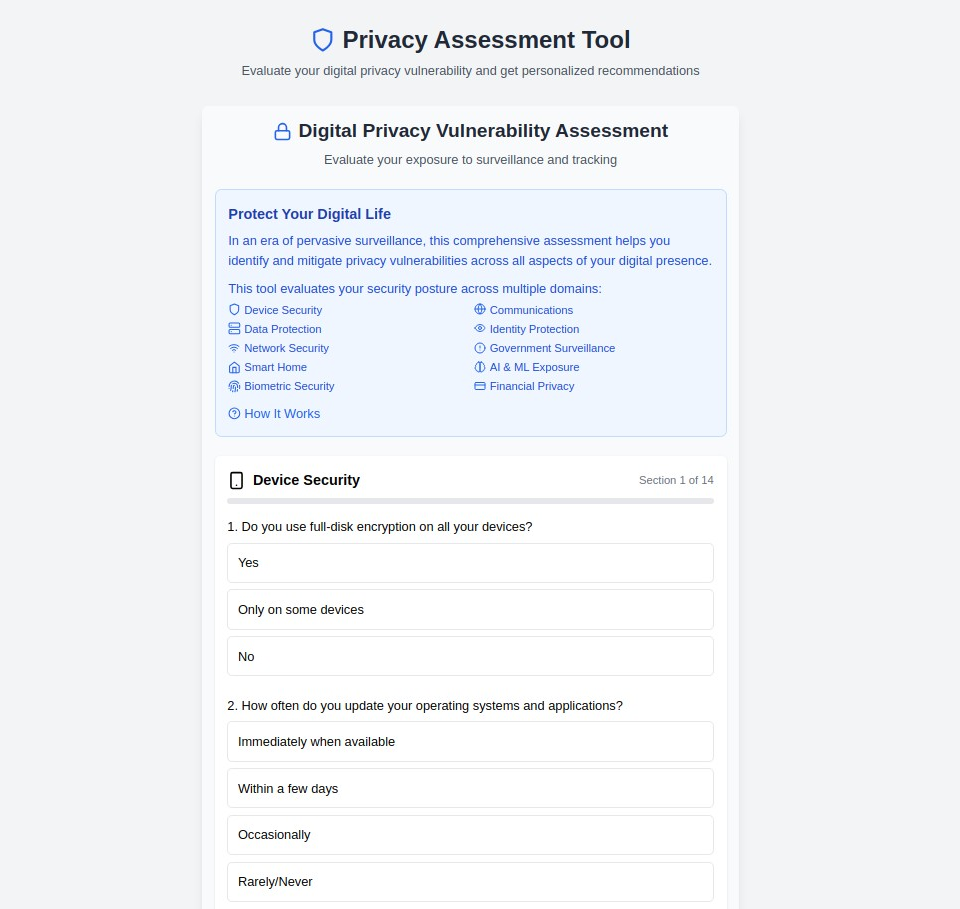
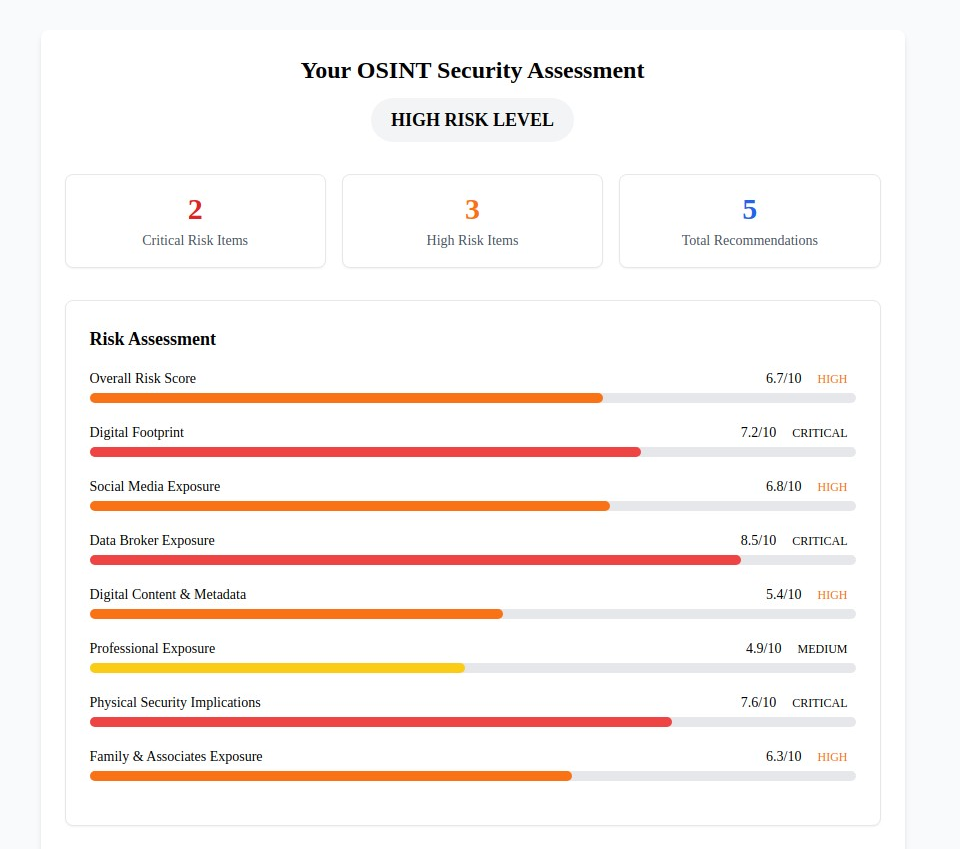
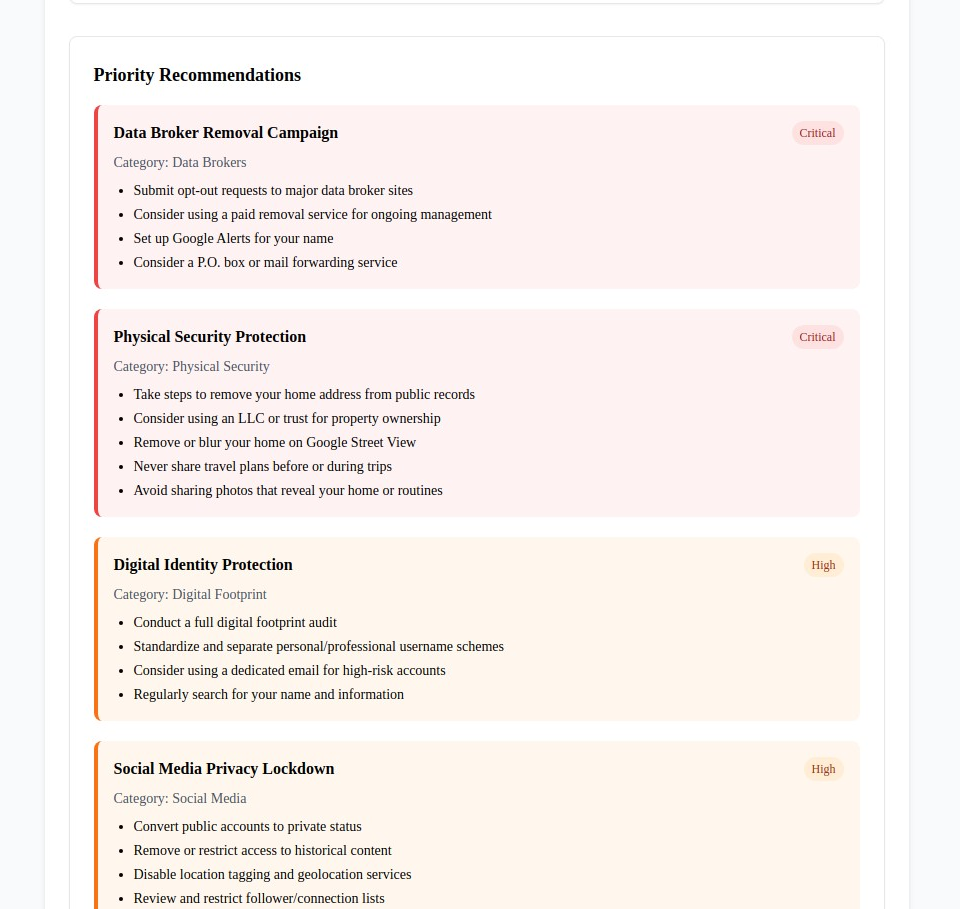
4. Open Source Intelligence (OSINT) Protection (osint.myprivacy.blog)
The Challenge: OSINT techniques can reveal shocking amounts of personal information from publicly available sources, putting individuals at risk from stalkers, criminals, and corporate surveillance.
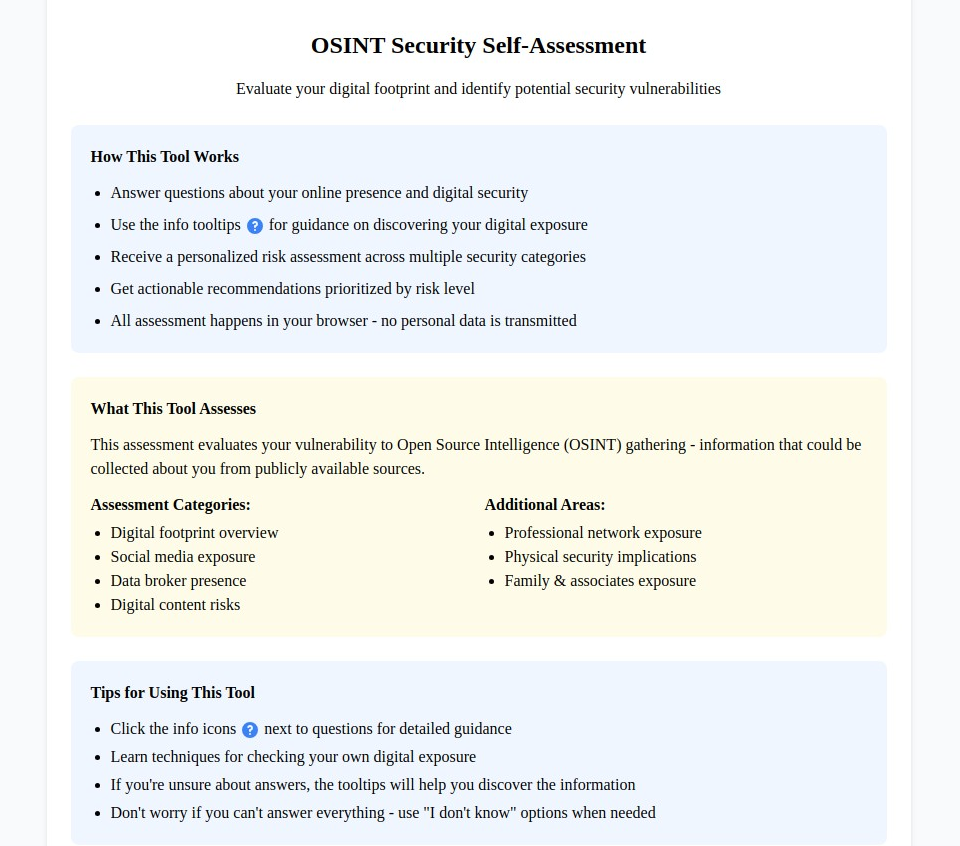
Our Solution: Education about OSINT techniques and comprehensive countermeasures to limit your exposure to intelligence gathering.
What You'll Find:
- Understanding how OSINT tools work and what they can discover about you
- Digital footprint reduction techniques and cleanup strategies
- Social media counter-surveillance measures
- Public records privacy and data broker removal
- Professional OSINT protection for high-risk individuals
- Corporate intelligence gathering defense strategies
Why It Matters: OSINT tools can compile detailed profiles using public data from social media, property records, court documents, and online activities. Understanding these techniques is the first step in defending against them.
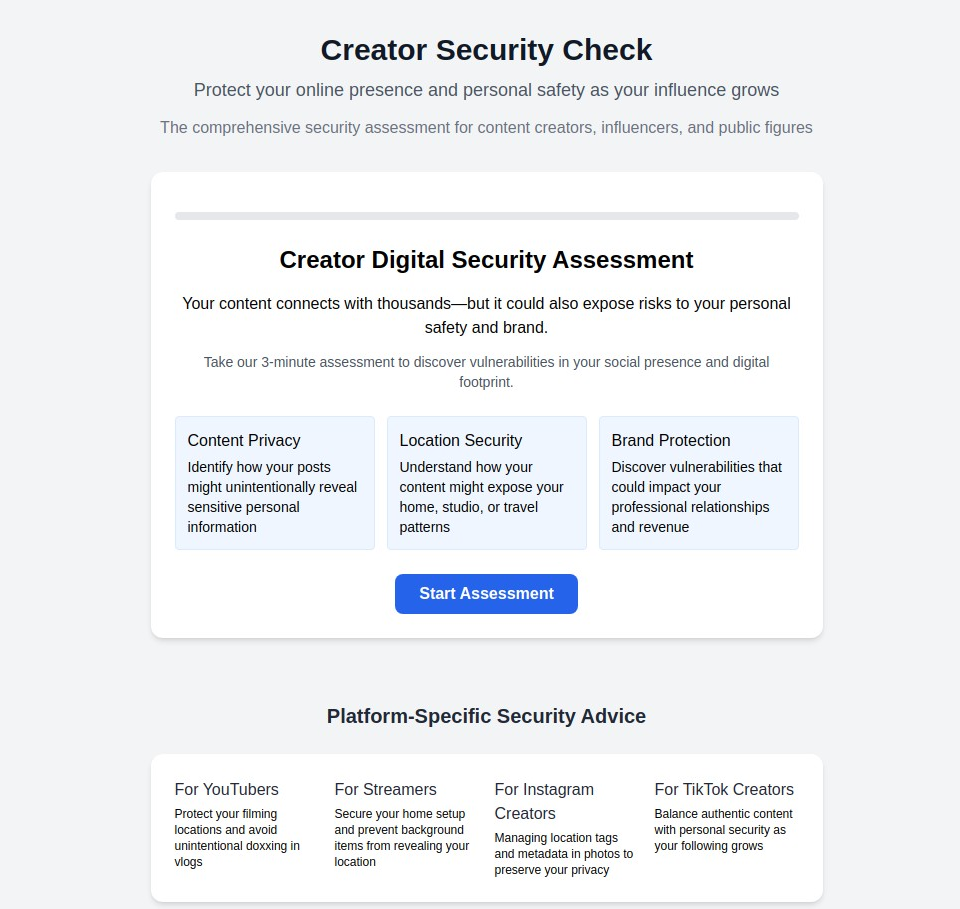
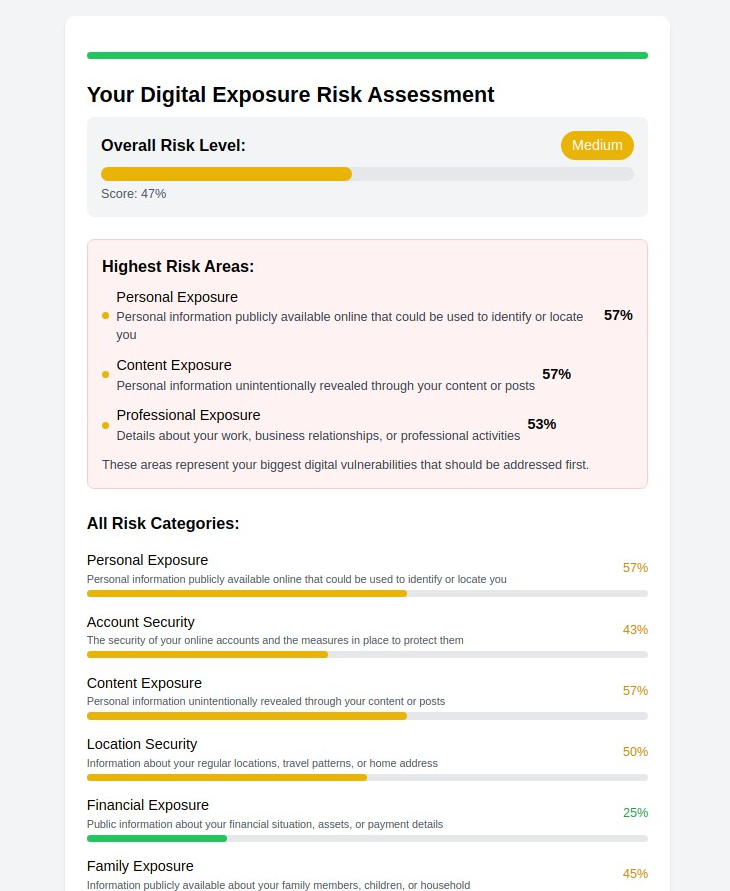
5. Influencer & Content Creator Privacy (influencer.myprivacy.blog)
The Challenge: Content creators and influencers face unique privacy risks including stalking, doxxing, account takeovers, and unwanted attention that can escalate to physical threats.
Our Solution: Specialized privacy strategies designed for public-facing individuals who must balance visibility with personal safety.
What You'll Find:
- Content creation privacy guidelines and safe sharing practices
- Advanced account security including multi-factor authentication strategies
- Legal protection tools including NDAs and business structure advice
- Physical security considerations for content creators
- Crisis management for privacy breaches and doxxing incidents
- Family and children protection for public figures
- Brand protection and reputation management privacy aspects
Why It Matters: Influencers share more personal information than traditional celebrities while often lacking the same level of professional security support. Our specialized guidance helps bridge this protection gap.
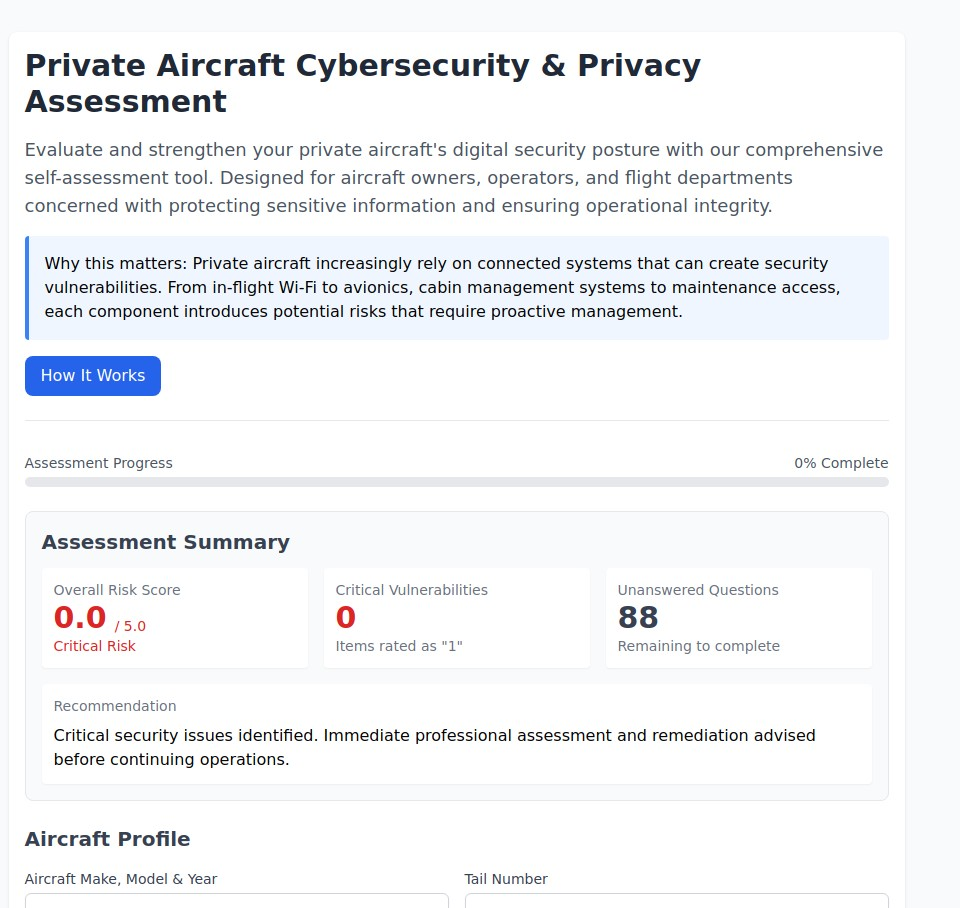
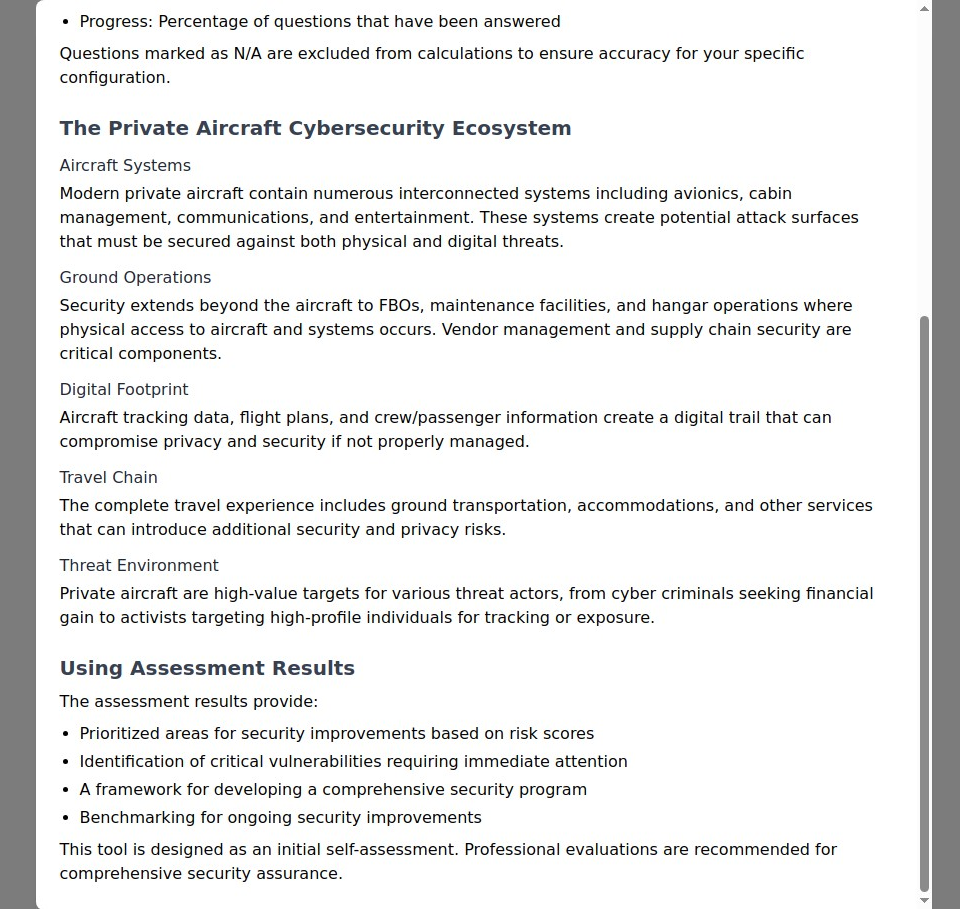
6. Aviation Privacy Protection (aircraft.myprivacy.blog)
The Challenge: Modern aircraft tracking systems like ADS-B create real-time surveillance of private flights, compromising the privacy and security of passengers and pilots.
Our Solution: Comprehensive aviation privacy strategies including legal tracking opt-outs and privacy-enhancing flight planning.
What You'll Find:
- FAA Privacy ICAO Address (PIA) program enrollment guides
- Limiting Aircraft Data Displayed (LADD) program instructions
- Third-party flight tracking opt-out procedures
- Private aviation security best practices
- International flight privacy considerations
- Business aviation privacy strategies
Why It Matters: Real-time flight tracking can expose travel patterns, business relationships, and personal activities. With over 300,000 general aviation aircraft in the US, privacy protection is essential for anyone flying privately.
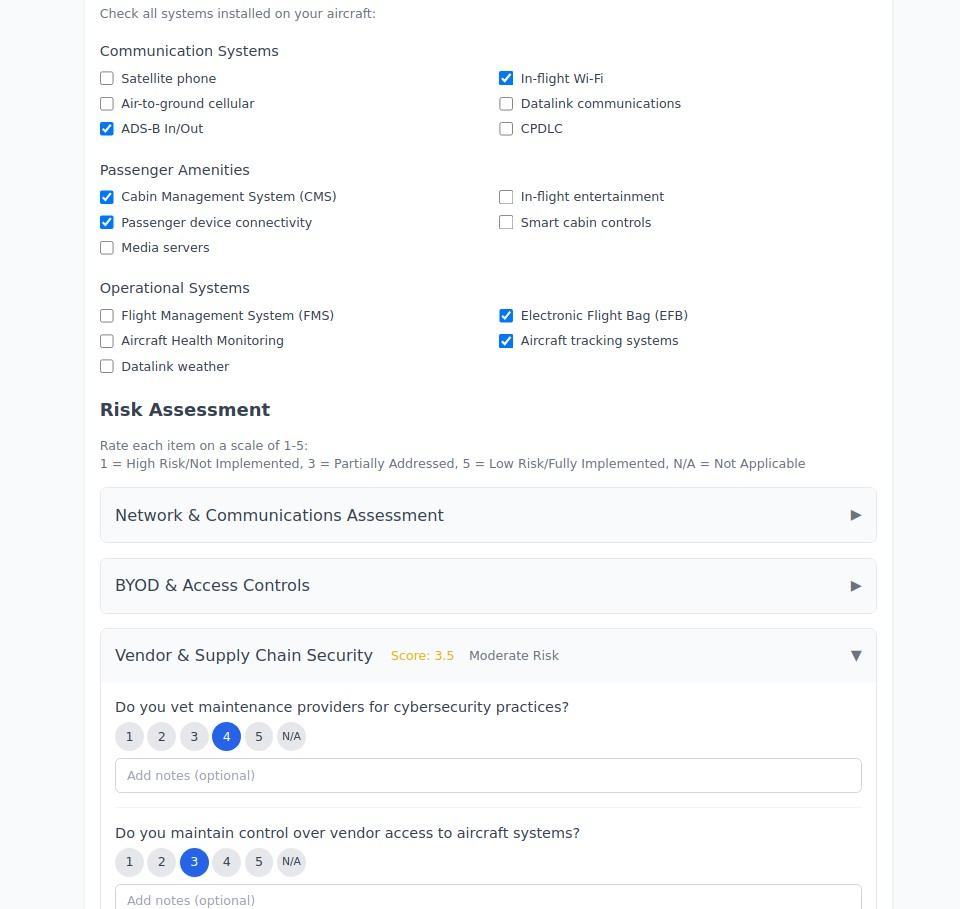
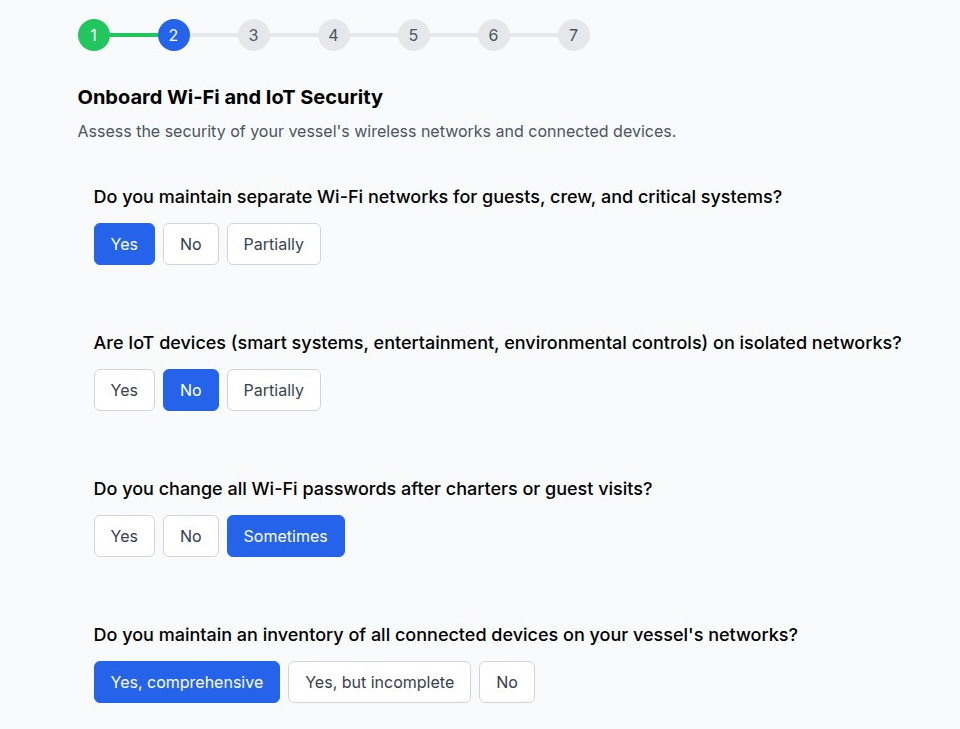
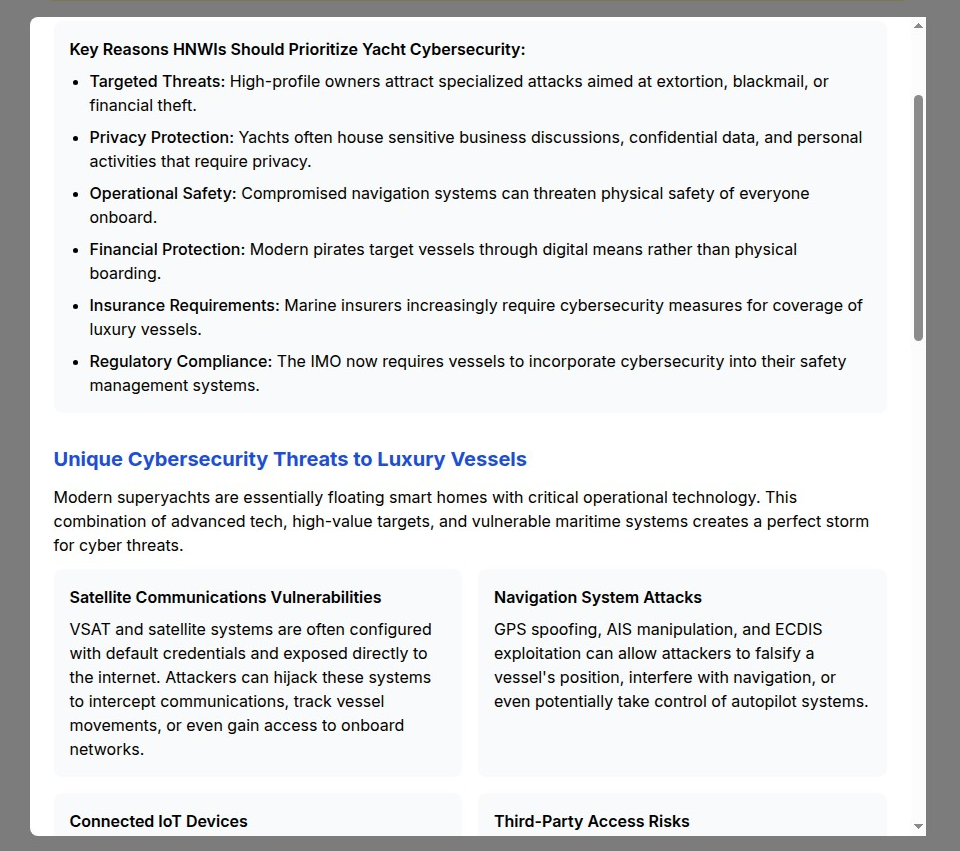
7. Luxury & High-Net-Worth Privacy (yacht.myprivacy.blog)
The Challenge: Wealthy individuals face sophisticated privacy threats including corporate espionage, kidnapping risks, asset tracking, and targeted social engineering.
Our Solution: Elite privacy protection strategies for luxury assets, high-value transactions, and ultra-high-net-worth lifestyle privacy.
What You'll Find:
- Luxury yacht privacy and security protocols
- Private residence and property privacy protection
- High-value asset anonymization techniques
- Offshore privacy strategies and legal structures
- Executive protection privacy considerations
- Luxury travel privacy and security planning
- Art collection and valuable asset privacy
Why It Matters: High-net-worth individuals are increasingly targeted by sophisticated threat actors. Luxury assets like yachts contain connected systems vulnerable to cyber attacks, while wealth visibility creates personal security risks.

Choosing Your Privacy Protection Strategy
Not every tool in our ecosystem will apply to your situation. Here's how to prioritize your privacy protection:
Start Here (Essential for Everyone):
- Social Media Privacy - Configure platform settings properly
- Identity Risk Assessment - Understand your current exposure
- Personal Privacy Tools - Implement basic digital hygiene
Add Based on Your Profile:
If you're a content creator or public figure:
- Influencer Privacy Protection
- Enhanced OSINT countermeasures
If you fly privately or own aircraft:
- Aviation Privacy Protection
- Enhanced travel privacy measures
If you're high-net-worth or own luxury assets:
- Luxury Privacy Protection
- Advanced anonymization techniques
If you're in a high-risk profession:
- Advanced OSINT protection
- Corporate counter-intelligence measures
The Future of Privacy Protection
Privacy threats continue evolving with new technologies and surveillance capabilities. Our ecosystem adapts to address emerging challenges including:
- AI-powered data aggregation and analysis
- Increased government surveillance capabilities
- IoT device proliferation and smart home vulnerabilities
- Cryptocurrency tracking and financial surveillance
- Biometric data collection and facial recognition
- Location tracking through multiple vectors
Getting Started with Your Privacy Protection
Privacy protection isn't about paranoia—it's about taking reasonable precautions appropriate to your risk level and lifestyle. Whether you're concerned about basic identity theft or need sophisticated protection against advanced threats, our specialized tools provide the guidance you need.

Your Next Steps:
- Assess Your Risk Profile - Identify which categories of threats apply to your situation
- Start with Fundamentals - Implement basic protections that benefit everyone
- Add Specialized Protection - Dive deeper into the specific tools that match your lifestyle and risk factors
- Stay Updated - Privacy threats evolve constantly; regular updates ensure continued protection
Remember: effective privacy protection is a process, not a destination. Start with the basics, gradually add specialized protections, and maintain your privacy posture as threats and technologies evolve.
The digital age doesn't have to mean the end of privacy. With the right knowledge, tools, and strategies, you can reclaim control over your personal information and maintain the privacy you deserve—regardless of your lifestyle, profession, or public profile.
Ready to enhance your privacy protection? Explore our specialized tools and start building your comprehensive privacy strategy today. Your digital freedom depends on the actions you take right now.












