The Complete Guide to Identity Risk Assessment & Protection: Defend Against the $12.5 Billion Identity Theft Crisis in 2025
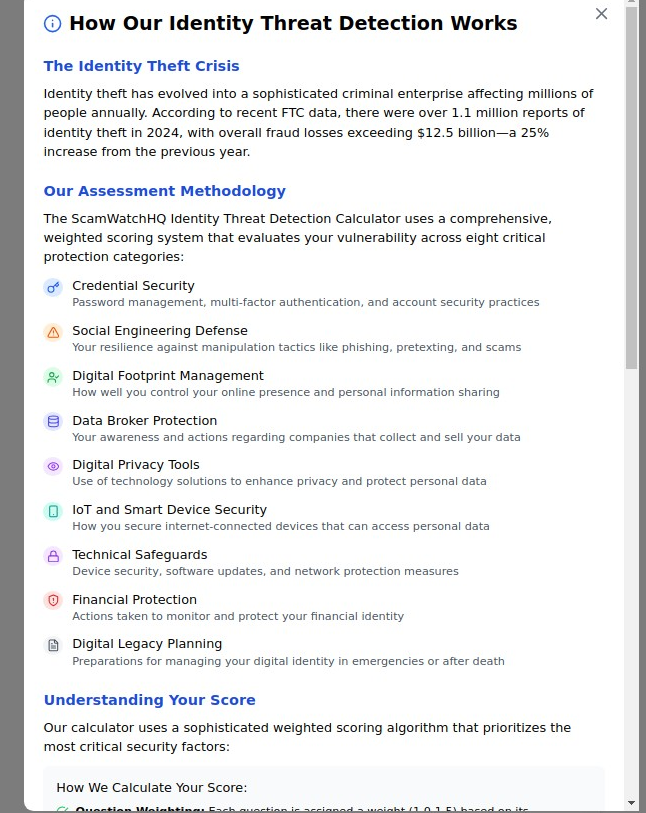
Identity theft has evolved from opportunistic crimes into a sophisticated criminal enterprise affecting millions of people annually. According to recent FTC data, there were over 1.1 million reports of identity theft in 2024, with overall fraud losses exceeding $12.5 billion—a staggering 25% increase from the previous year. What makes this crisis particularly alarming is that most victims don't discover the theft until months after criminals have already caused significant damage to their financial lives and credit histories.
The challenge isn't just the scale of identity theft—it's the sophistication of modern attacks that exploit multiple vulnerabilities simultaneously. Today's identity thieves combine traditional methods like mail theft and dumpster diving with advanced digital techniques including social media reconnaissance, data broker exploitation, and social engineering attacks that can deceive even security-conscious individuals.
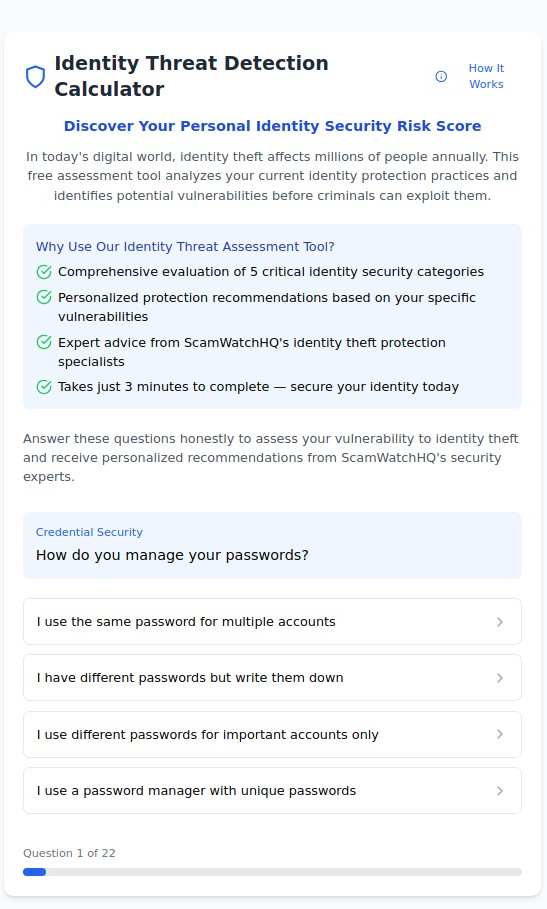
This comprehensive guide provides evidence-based strategies to assess your identity theft risk, implement proportional protection measures, and create early warning systems that detect threats before they become devastating losses. Whether you're concerned about basic identity protection or need advanced strategies for high-risk situations, these proven techniques will dramatically strengthen your identity security posture.
Understanding Your Identity Threat Landscape
Modern identity theft operates across multiple attack vectors that most people never consider. Criminals don't just steal wallets or intercept mail—they systematically gather information from dozens of sources to build comprehensive identity profiles that can bypass traditional security measures.

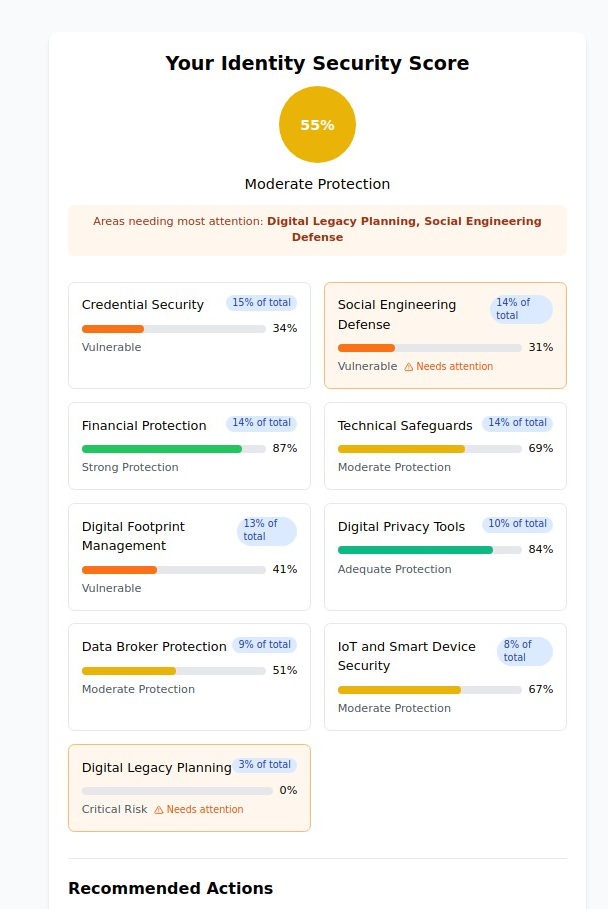
The Eight Critical Identity Security Categories:
Our research analyzing thousands of identity theft cases reveals that comprehensive protection requires addressing vulnerabilities across eight critical categories. Each category represents a different attack surface that criminals exploit, and weakness in any area can compromise your entire identity security strategy.






