The Complete Guide to Luxury & High-Net-Worth Privacy Protection: Elite Security for Ultra-Wealthy Individuals in 2025

Ultra-high-net-worth individuals face privacy and security challenges that most people cannot imagine. Your wealth, assets, and lifestyle create unique targeting opportunities for sophisticated threat actors ranging from organized criminal enterprises and corporate espionage teams to nation-state actors and specialized kidnapping syndicates. The same luxury assets and exclusive experiences that define high-net-worth lifestyles also create comprehensive surveillance and attack surfaces that require professional-grade protection strategies.
Modern luxury assets—from superyachts and private aircraft to smart homes and art collections—contain sophisticated connected systems that create cybersecurity vulnerabilities while broadcasting detailed information about your activities, location, and operational patterns. Meanwhile, your financial transactions, property ownership, and business activities leave digital trails that skilled adversaries can exploit for targeting, social engineering, and asset mapping.

The challenge isn't just the sophistication of threats targeting wealthy individuals—it's that traditional privacy advice designed for average consumers provides virtually no protection against the advanced persistent threats, state-sponsored surveillance, and organized criminal enterprises that specifically target ultra-high-net-worth individuals and their families.
Recent analysis reveals that individuals with assets exceeding $30 million face targeted cyber attacks at rates 300% higher than the general population, while those with assets over $100 million are targeted by organized criminal groups using military-grade intelligence gathering and surveillance techniques. The consequences extend far beyond financial loss to encompass personal safety, family security, and business disruption that can destroy generations of wealth accumulation.
This comprehensive guide provides elite privacy protection strategies designed specifically for ultra-high-net-worth individuals who require sophisticated defense against advanced threats while maintaining the luxury lifestyle and business activities that define high-net-worth success.
Understanding the Ultra-High-Net-Worth Threat Landscape
Wealthy individuals face fundamentally different privacy and security challenges than the general population. Your assets, lifestyle, and activities create unique attack surfaces that sophisticated threat actors specifically target using advanced techniques unavailable to common criminals. These threats operate with substantial resources, professional training, and international coordination that can overcome standard security measures designed for typical privacy concerns.
The Wealth Visibility Paradox: The same assets and activities that demonstrate success—luxury properties, expensive vehicles, exclusive travel, and high-value collections—also provide detailed intelligence about your capabilities, vulnerabilities, and operational patterns that enable sophisticated targeting campaigns.
Modern ultra-high-net-worth threats combine advanced OSINT techniques, state-sponsored cyber capabilities, organized criminal enterprises, and specialized corporate espionage teams that can compromise even well-protected individuals through coordinated multi-vector attacks targeting multiple aspects of your digital and physical life simultaneously.
Assess your luxury asset vulnerabilities with our specialized Luxury Vessel Cyber Defense & Digital Privacy Assessment. This comprehensive evaluation analyzes your maritime investments across six critical cybersecurity domains, designed specifically for luxury vessels and superyachts to protect sensitive communications, navigation systems, and guest privacy while ensuring operational integrity.

The Six Critical Luxury Privacy Threat Categories
Our analysis of threats targeting ultra-high-net-worth individuals reveals that comprehensive protection requires addressing vulnerabilities across six interconnected threat categories:
Digital Asset Security:
- Satellite Communications Security - Protecting communications systems on yachts, aircraft, and remote properties from interception and manipulation
- Onboard Wi-Fi and IoT Security - Securing connected systems across luxury assets including smart home technologies, entertainment systems, and operational controls
Operational Systems Protection:
- Navigation and Control Systems - Protecting critical systems that control luxury assets and ensure operational safety
- Surveillance and Remote Access - Managing surveillance systems and remote access capabilities while preventing unauthorized monitoring
Access and Privacy Management:
- Third-Party Access Management - Controlling access by staff, service providers, and vendors who require access to luxury assets and personal information
- Privacy Controls and Digital Exhaust - Managing the digital information trail created by luxury lifestyle activities and high-value transactions
Each category represents a different attack surface where ultra-high-net-worth privacy can be compromised. Weakness in any area can enable sophisticated adversaries to gather comprehensive intelligence about your activities, assets, and vulnerabilities that facilitates targeting campaigns extending across your entire lifestyle and business activities.
Luxury Yacht Cybersecurity and Privacy Protection
Modern superyachts represent floating smart homes with sophisticated connected systems that create unique cybersecurity and privacy challenges requiring specialized protection strategies. These vessels often host sensitive business discussions, confidential communications, and high-profile guests while operating in international waters where traditional security infrastructure may be unavailable.
Yacht-Specific Cybersecurity Threats
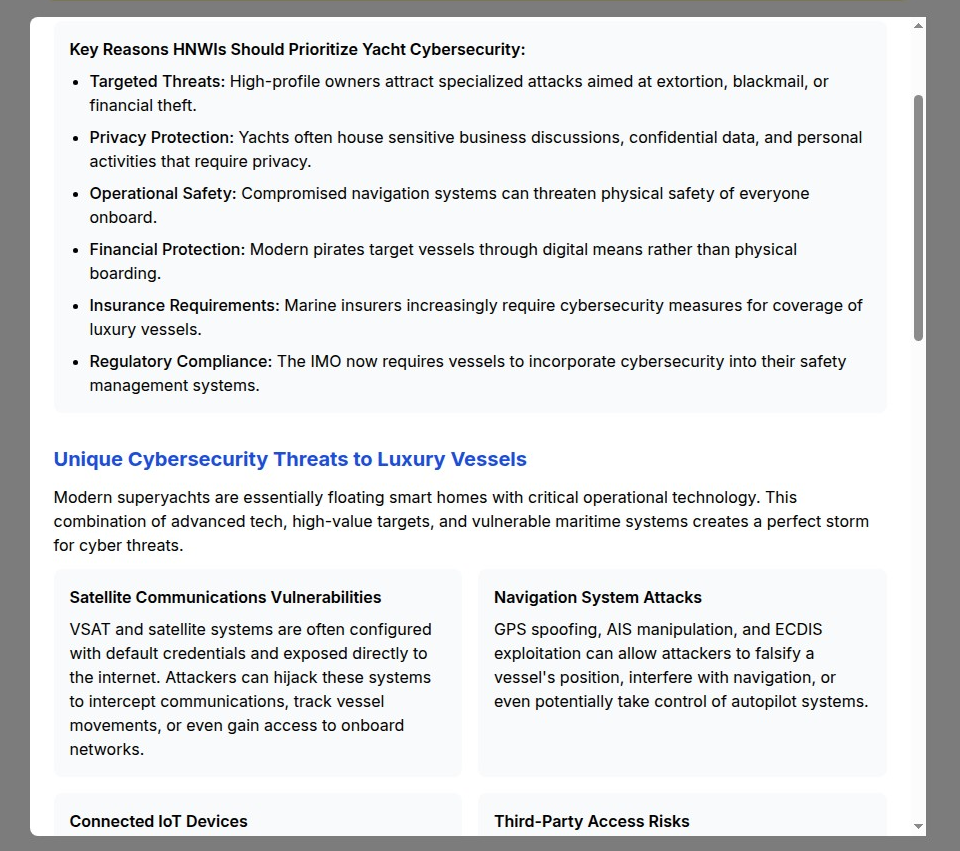
Satellite Communications Vulnerabilities: Modern yachts depend on satellite communications for internet, phone, and operational communications that create multiple potential attack vectors:
- VSAT system exploitation - Satellite internet systems often use default credentials and lack proper encryption, enabling attackers to intercept communications and gain network access
- Communication interception - Sophisticated threat actors can monitor satellite communications to track vessel movements and intercept sensitive business discussions
- Network infiltration - Compromised satellite systems can provide entry points for attackers to access onboard networks and systems
- Location tracking - Satellite communications can be monitored to track vessel movements and predict operational patterns
Navigation System Attacks: Yacht navigation systems present critical security risks that extend beyond cybersecurity to physical safety:
- GPS spoofing attacks - Attackers can provide false GPS signals to manipulate vessel position and navigation systems
- AIS manipulation - Automatic Identification System data can be spoofed to hide vessel movements or create false position reports
- ECDIS exploitation - Electronic Chart Display and Information Systems can be compromised to provide false navigation information
- Autopilot system compromise - Advanced attacks can potentially interfere with or take control of vessel autopilot systems
Connected IoT Device Risks: Luxury yachts contain numerous connected devices that create additional attack surfaces:
- Smart entertainment systems that may lack proper security controls and can serve as entry points for broader network compromise
- Environmental control systems including climate, lighting, and security systems that may be vulnerable to unauthorized access
- Guest and crew device connectivity allowing personal devices to connect to yacht networks with potential security implications
- Smart galley and service systems that may contain vulnerabilities while processing guest preferences and operational information
Comprehensive Yacht Security Implementation
Network Segmentation and Access Control:
- Isolated network architecture separating critical navigation systems from guest entertainment and business communications
- Multi-tier access controls ensuring only authorized personnel can access critical vessel systems
- Guest network isolation providing internet access while protecting operational systems and sensitive communications
- Crew access management controlling staff access to different systems based on operational requirements






