The Complete Guide to Social Media Privacy Protection: Secure Your Digital Life Across All Platforms in 2025
Social media has fundamentally transformed how we communicate, share experiences, and build relationships. Yet with over 4.8 billion users worldwide sharing unprecedented amounts of personal data, these platforms have become goldmines for data harvesting, surveillance, and privacy violations. Recent revelations about Meta training AI models on user content without explicit consent highlight a disturbing truth: your social media activity is being monetized in ways you never agreed to.

The challenge isn't just about privacy settings—it's about understanding the complex web of data collection, cross-platform tracking, and algorithmic analysis that occurs every time you engage with social media. Most users operate with default settings that prioritize platform profits over personal privacy, creating massive vulnerabilities in their digital lives.
This comprehensive guide provides platform-specific strategies to reclaim control over your social media privacy, protect your personal data, and secure your digital presence across all major networks. Whether you're a casual user or a content creator, these evidence-based techniques will dramatically reduce your privacy risk profile.
t
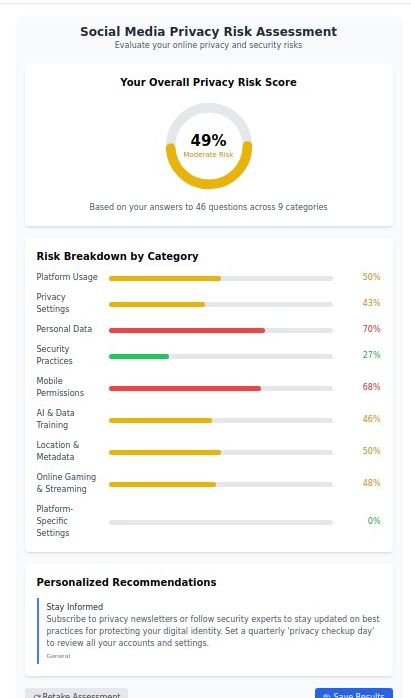
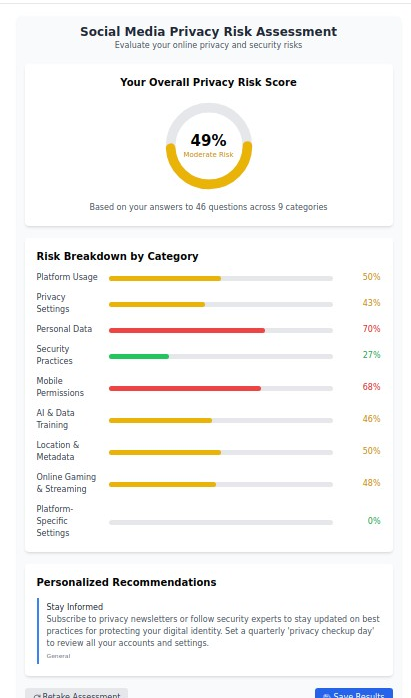
Understanding Your Social Media Privacy Risk Profile
Before diving into platform-specific protections, it's crucial to understand your current exposure level. Modern social media privacy risks extend far beyond what you post—they encompass your device permissions, cross-platform data sharing, location tracking, AI training data usage, and behavioral analytics.
Our research analyzing thousands of social media users reveals that the average person has a moderate to high privacy risk score across nine critical categories:
- Platform Usage Patterns - How your activity creates data profiles
- Privacy Settings Configuration - Whether you've optimized built-in protections
- Personal Data Exposure - What sensitive information you're inadvertently sharing
- Security Practices - Your account protection measures
- Mobile Permissions - What device access you've granted
- AI & Data Training - How your content is used for machine learning
- Location & Metadata - Geographic and technical data exposure
- Cross-Platform Integration - How platforms share your information
- Platform-Specific Vulnerabilities - Unique risks on each network
Take our free Social Media Privacy Risk Assessment to discover your specific vulnerabilities and receive personalized protection recommendations. This confidential analysis evaluates your practices across all major platforms and provides actionable insights for improvement.
The Hidden Costs of Social Media Privacy Neglect
The consequences of inadequate social media privacy protection extend far beyond targeted advertising. Consider these real-world impacts:
Professional Consequences: 70% of employers research candidates on social media, and 54% have decided not to hire someone based on their social media presence. Poor privacy settings can expose personal information that damages professional opportunities.
Personal Safety Risks: Location data, check-ins, and photo metadata can enable stalking, burglary, and physical threats. Content creators and public figures face particularly elevated risks from inadequate privacy protection.
Financial Exploitation: Personal information gathered from social media is increasingly used for social engineering attacks, identity theft, and financial fraud. Even seemingly innocent posts can provide answers to security questions or reveal behavioral patterns.
Relationship and Family Impact: Privacy breaches can expose family members, damage relationships, and compromise children's safety. Cross-platform data sharing can reveal information about contacts who never consented to surveillance.
Long-term Reputation Damage: Social media content persists far longer than most users realize. Poor privacy practices today can impact opportunities, relationships, and reputation for years to come.


Platform-Specific Privacy Protection Strategies
Facebook/Meta: Comprehensive Privacy Lockdown
Meta's ecosystem presents unique challenges due to its integration across Facebook, Instagram, WhatsApp, and Messenger, plus extensive third-party data sharing partnerships.
Essential Privacy Configurations:
Account Privacy Settings:
- Navigate to Settings & Privacy → Privacy → Future Posts and set default audience to "Friends" only
- Review "Limit Past Posts" to restrict old content to friends only
- Disable "Public Post Comments" to prevent strangers from commenting
- Turn off "Story Sharing" to prevent friends from sharing your stories








