The Stingray Controversy: Uncovering the Secrets of Cell Phone Surveillance and the Battle for Privacy
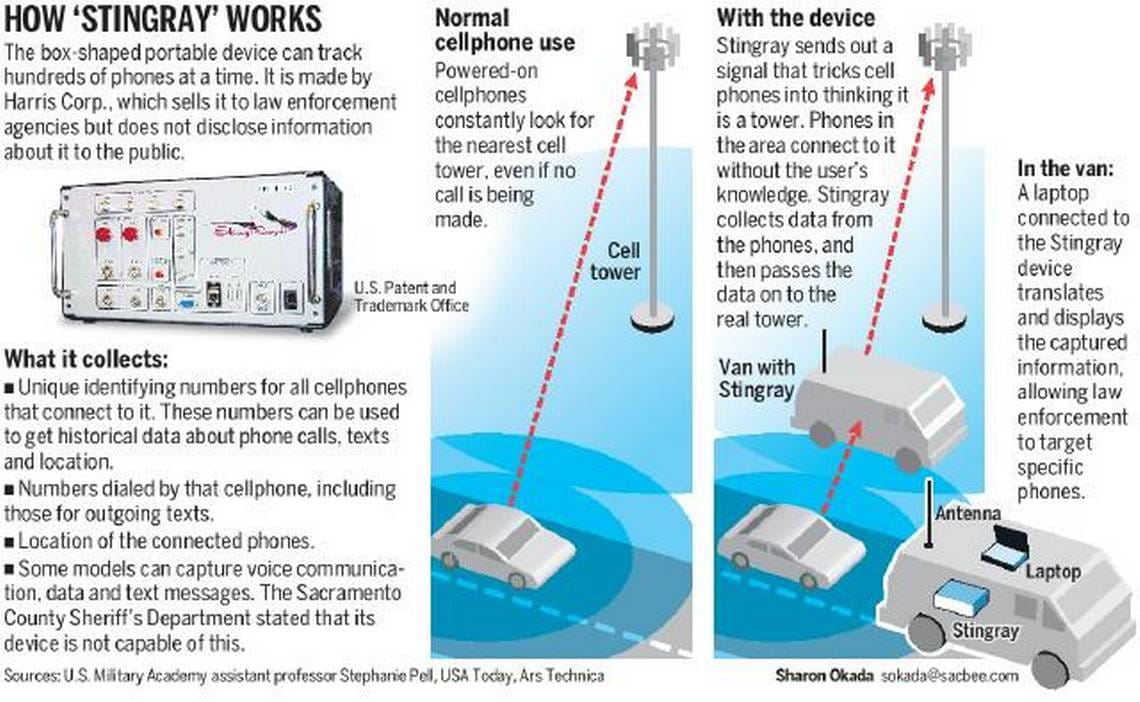
The use of cell phone surveillance technology, commonly known as Stingrays, has been a topic of controversy in recent years. These devices, also referred to as International Mobile Subscriber Identity (IMSI) catchers, have been employed by law enforcement agencies to track and locate cell phones. However, the secrecy surrounding their use and the potential for privacy violations have raised significant concerns among privacy advocates and the general public.

How Stingrays Work
Stingrays operate by mimicking cell phone towers, emitting signals that force nearby cell phones to connect to them. This allows law enforcement to gather information about the location and identity of cell phones within a specific radius. The devices can be used to track a suspect's phone, but they also collect data from the phones of innocent bystanders in the area. This indiscriminate data collection has sparked concerns about the violation of Fourth Amendment rights, which protect individuals from unreasonable searches and seizures.

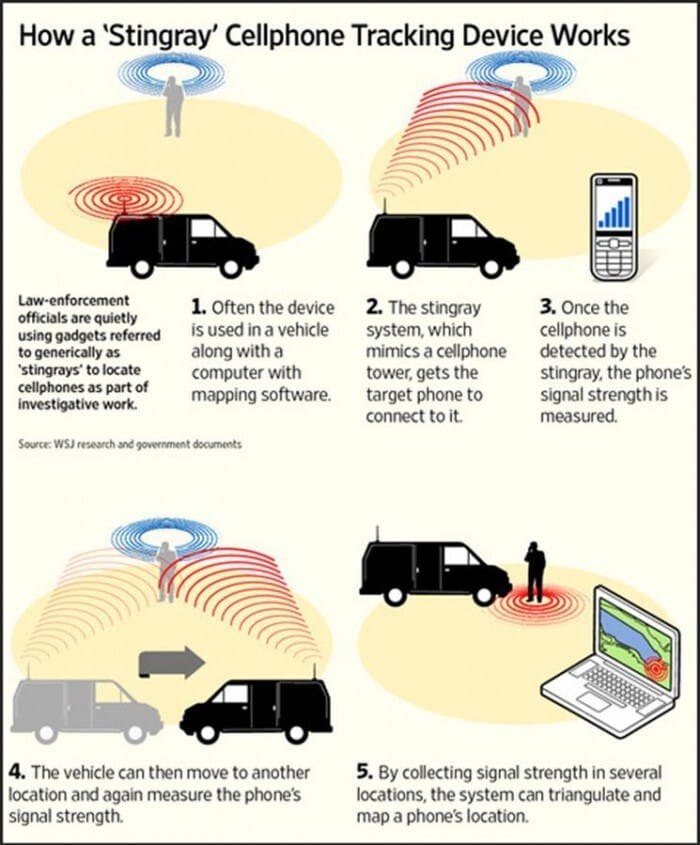
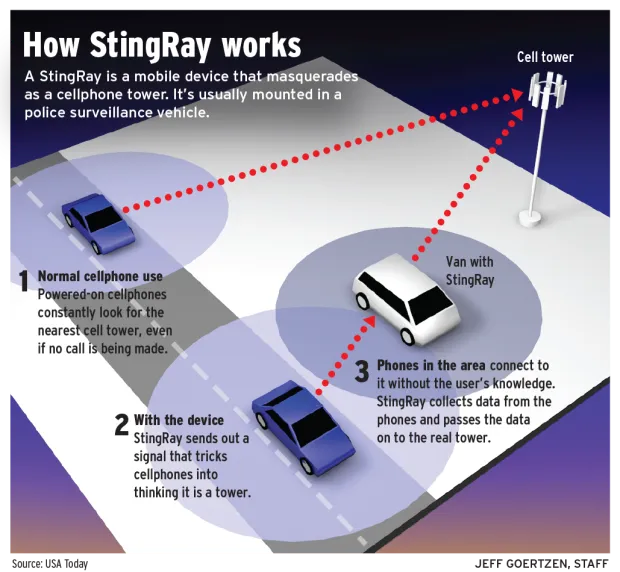



The Rigmaiden Case: A Landmark in Stingray Controversy
The United States v. Rigmaiden case has been a pivotal moment in the Stingray controversy. The case involved the use of a Stingray device to track a suspect's cell phone without a warrant. The court's ruling in this case has significant implications for the use of Stingray technology and the protection of privacy rights.
Legal Gray Area and Constitutional Violations
The use of Stingray devices by law enforcement agencies has been criticized for violating the Fourth Amendment. The devices collect data from innocent bystanders, which is not protected by a warrant. This raises questions about the legality of such searches and the potential for abuse of power.
Secrecy and Lack of Transparency
One of the most significant concerns surrounding Stingray technology is the secrecy and lack of transparency surrounding its use. Law enforcement agencies have been known to conceal the use of Stingrays in court documents and from judges. This lack of transparency has led to criticism from privacy advocates and lawmakers.
- Scope of data collection:
- Stingrays collect data indiscriminately from all nearby cellular devices, not just the target. This makes them more invasive than targeted wiretaps or GPS tracking of specific suspects.
- Other technologies like security cameras or license plate readers also collect bulk data, but are typically limited to public spaces.
- Type of data collected:
- Stingrays can collect location data, device identifiers, and in some cases call/text content.
- This is more comprehensive than technologies that only track location (like GPS ankle monitors) or only capture visual data (like body cameras).
- Legal requirements:
- Stingray use operates in a legal "gray area" with inconsistent warrant requirements across jurisdictions.
- More established technologies like wiretaps typically have clearer legal frameworks governing their use.
- Secrecy:
- Law enforcement agencies have gone to great lengths to keep stingray capabilities secret, even dropping cases to avoid disclosing their use.
- While details of other surveillance tools may be protected, the existence and general capabilities of technologies like body cameras or dash cams are widely known.
- Cost and accessibility:
- Stingrays are expensive ($400,000+ per unit) and primarily used by larger agencies or through federal grants.
- Technologies like body cameras or automated license plate readers are more affordable and widely adopted by law enforcement.
- Technological sophistication:
- Stingrays actively mimic cell towers to intercept communications.
- This is more advanced than passive collection methods like security cameras or recording devices.
- Potential for abuse:
- The broad data collection of stingrays creates significant privacy concerns, especially for bystanders.
- While any technology can be misused, the secretive nature and lack of oversight for stingrays is particularly concerning to privacy advocates.
Governmental Agencies' Improper Use of Stingrays
The use of Stingrays during protests, such as the Black Lives Matter movement, has raised concerns about the misuse of this technology. The devices have been used to track and monitor protesters, potentially infringing on their right to free assembly and speech.
- Scope and precision:
- Stingrays can track specific individuals with high precision by intercepting cellular signals.
- They are more targeted than technologies like security cameras or license plate readers, which collect bulk data in public areas.
- Data collection capabilities:
- Stingrays can collect a wide range of data, including location information, device identifiers, and potentially call/text content.
- This provides more comprehensive intelligence than single-purpose tools like GPS trackers or wiretaps.
- Covert operation:
- Stingrays can operate covertly, mimicking cell towers without alerting targets.
- This gives them an advantage over more visible surveillance methods like physical tailing or marked police vehicles.
- Real-time tracking:
- Stingrays allow for real-time location tracking of mobile devices.
- This can be more effective for active pursuits compared to technologies that rely on historical data analysis.
- Range and mobility:
- Stingrays can be mobile (e.g., mounted in vehicles) and cover a significant area.
- This flexibility can be advantageous compared to fixed surveillance installations.
- Indiscriminate data collection:
- Stingrays collect data from all nearby devices, not just the target.
- While this raises privacy concerns, it can provide additional intelligence or help identify associates of suspects.
- Limitations:
- Stingrays are only effective against cellular devices and may be thwarted by advanced counter-surveillance techniques.
- Other technologies may be more suitable for different scenarios (e.g., facial recognition for identifying suspects in crowds).
- Legal and ethical considerations:
- The secretive nature and legal gray area of stingray use can complicate their deployment and the admissibility of evidence.
- Other surveillance technologies with clearer legal frameworks may be preferable in some cases.
Overall, stingrays appear to be highly effective for tracking and gathering intelligence on suspects using cellular devices. However, their effectiveness must be weighed against privacy concerns, legal challenges, and the specific requirements of each investigation. Law enforcement often uses stingrays in conjunction with other surveillance technologies to build a comprehensive picture of criminal activities.
Calls for Action and Reform
The controversy surrounding Stingray technology has led to calls for action and reform. Lawmakers and privacy advocates are pushing for greater transparency and accountability in the use of these devices. The public has a right to know how and when Stingrays are being used, and what measures are in place to protect privacy rights.
Conclusion
The Stingray controversy highlights the ongoing struggle between privacy and security in the digital age. While these devices can be useful tools for law enforcement, their use must be balanced against the need to protect individual privacy rights. Greater transparency and accountability are essential to ensuring that Stingray technology is used in a way that respects the Constitution and the rights of citizens.
References:
[1] Samantha Hazen, "Upholding Citizens' Privacy in the Use of Stingray Technology: Is New York Behind?" Pace Law Review, vol. 37, no. 1, 2017.
[2] "StingRay Technology and Reasonable Expectations of Privacy in the Internet of Everything," Federalist Society Review, 2016.
[3] "Surreal Stingray Secrecy: Uncovering the FBI's Surveillance Tech Secrecy Agreements," ACLU, 2021.
[4] Alex Lemberg, "Stingrays: A 'Legal Gray Area' and How Law Enforcement Can Violate Your Fourth Amendment Rights," 2022.
[5] "Stingrays: The Biggest Technological Threat to Cell Phone Privacy You Don't Know About," Electronic Frontier Foundation, 2012.
Citations:
[1] https://digitalcommons.pace.edu/cgi/viewcontent.cgi?article=1942&context=plr
[2] https://fedsoc.org/fedsoc-review/stingray-technology-and-reasonable-expectations-of-privacy-in-the-internet-of-everything
[3] https://www.aclu.org/news/privacy-technology/surreal-stingray-secrecy-uncovering-the-fbis-surveillance-tech-secrecy-agreements
[4] https://www.alexlemberg.com/blog/stingrays-a-legal-gray-area-and-how-law-enforcement-can-violate-your-fourth-amendment-rights
[5] https://www.eff.org/deeplinks/2012/10/stingrays-biggest-unknown-technological-threat-cell-phone-privacy






