Women's Safety App Tea Suffers Massive Data Breach, Users' IDs Exposed on 4chan
Privacy Nightmare Hits Viral Dating Safety Platform
The women-only dating safety app Tea, which rocketed to the top of Apple's App Store charts this week, has suffered a catastrophic data breach that exposed tens of thousands of users' driver's licenses, selfies, and personal verification photos to users on the anonymous messaging board 4chan.
What is Tea?
Tea is a controversial app designed exclusively for women to anonymously share experiences and warnings about men they've dated. The platform requires strict identity verification—users must upload both a selfie and a government-issued ID to prove they are women before gaining access to the community.
The app's premise is simple but polarizing: women can search for men by photo and location, then view anonymous reviews and "red flags" or "green flags" posted by other users who have dated them. Think of it as a combination of Yelp and a background check service, but for romantic partners.
— vx-underground (@vxunderground) July 26, 2025
The Security Disaster
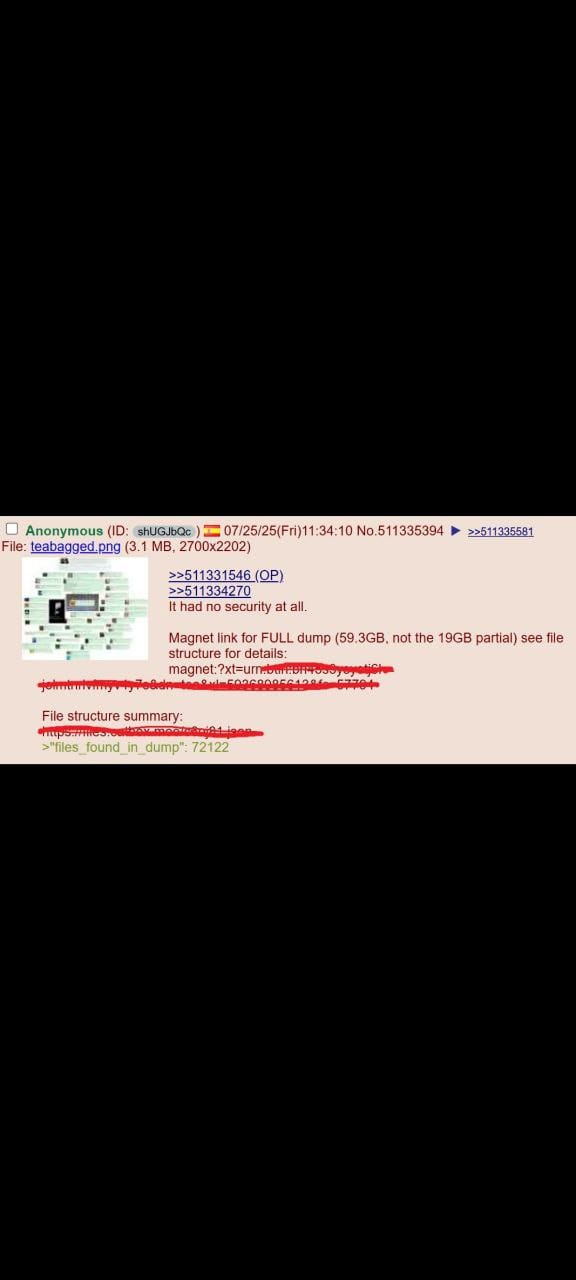
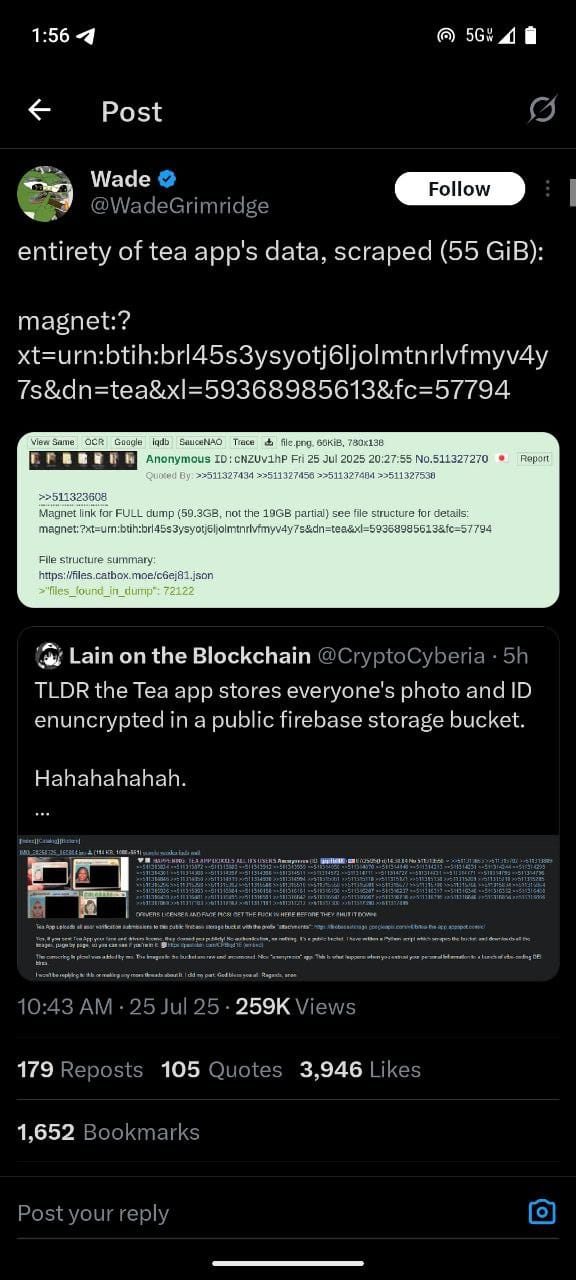
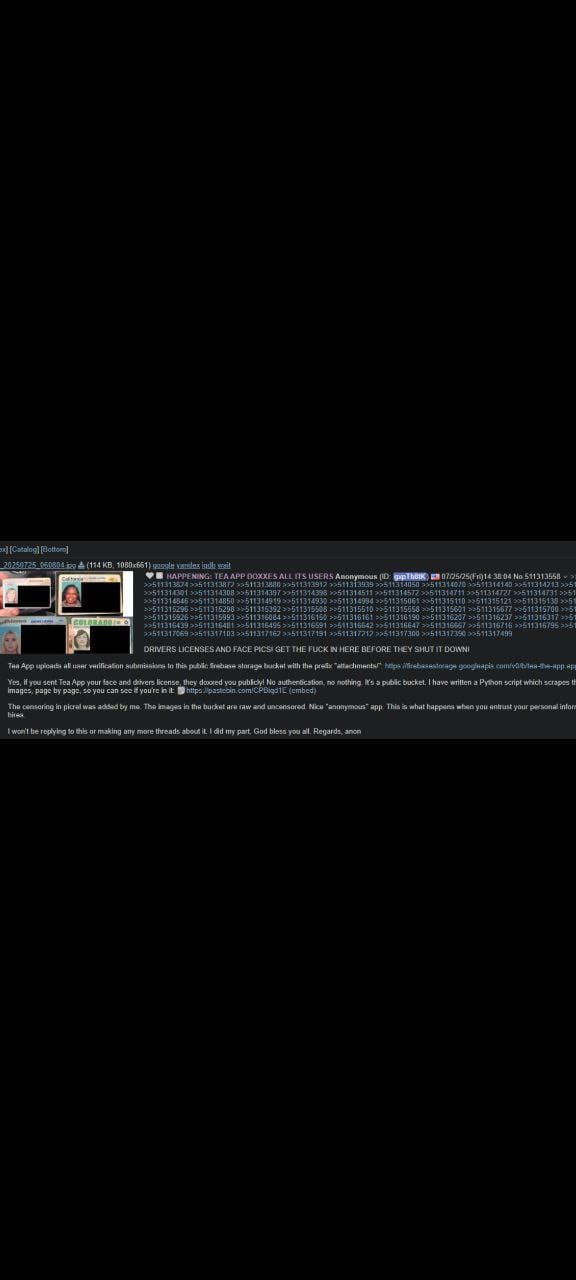
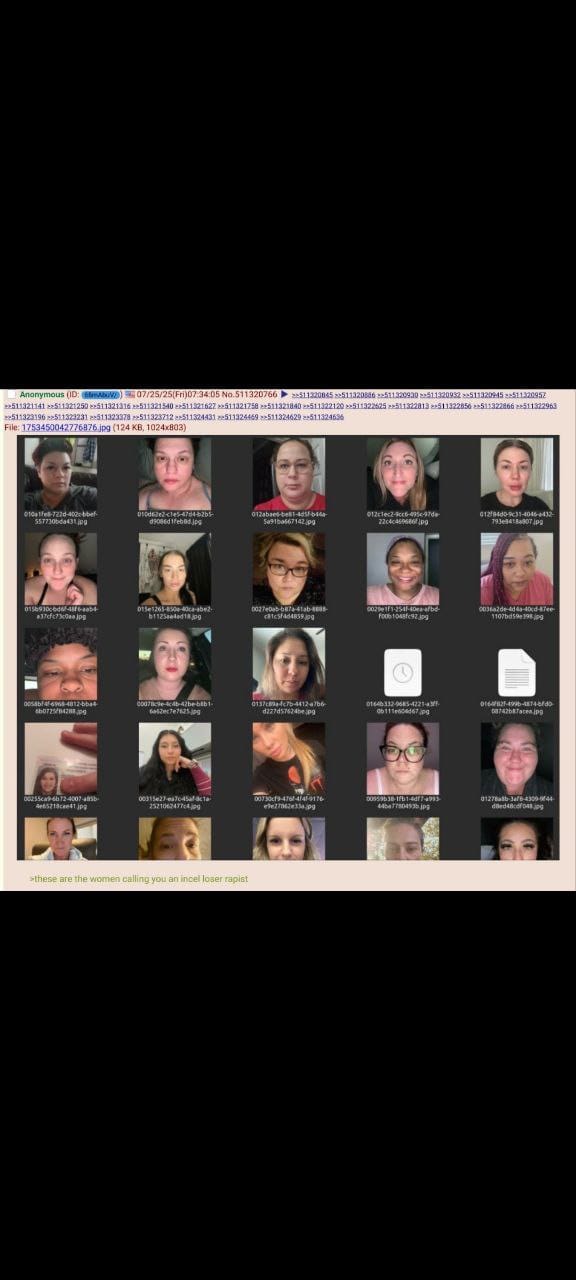
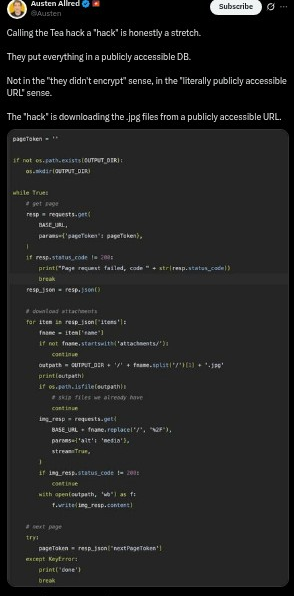
On July 25, 2025, users on 4chan discovered that Tea's entire user database was stored in a completely unsecured Google Firebase storage bucket. No password, no authentication, no security measures whatsoever—just a public URL that anyone could access.
"Yes, if you sent Tea App your face and drivers license, they doxxed you publicly! No authentication, no nothing. It's a public bucket," read one 4chan post that included the vulnerable database link.
The thread, which has since been deleted, contained messages like "DRIVERS LICENSES AND FACE PICS! GET THE F*** IN HERE BEFORE THEY SHUT IT DOWN!" as users scrambled to download as much personal data as possible.
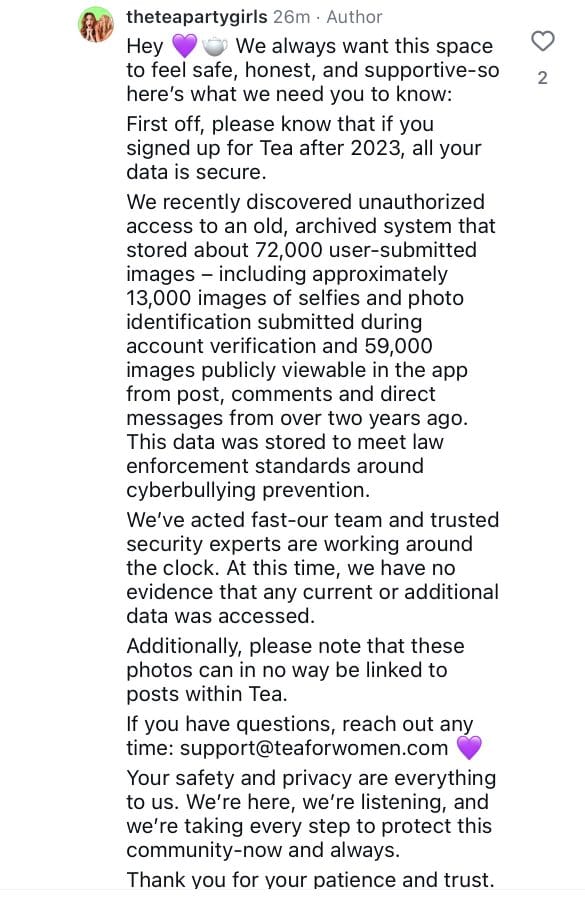
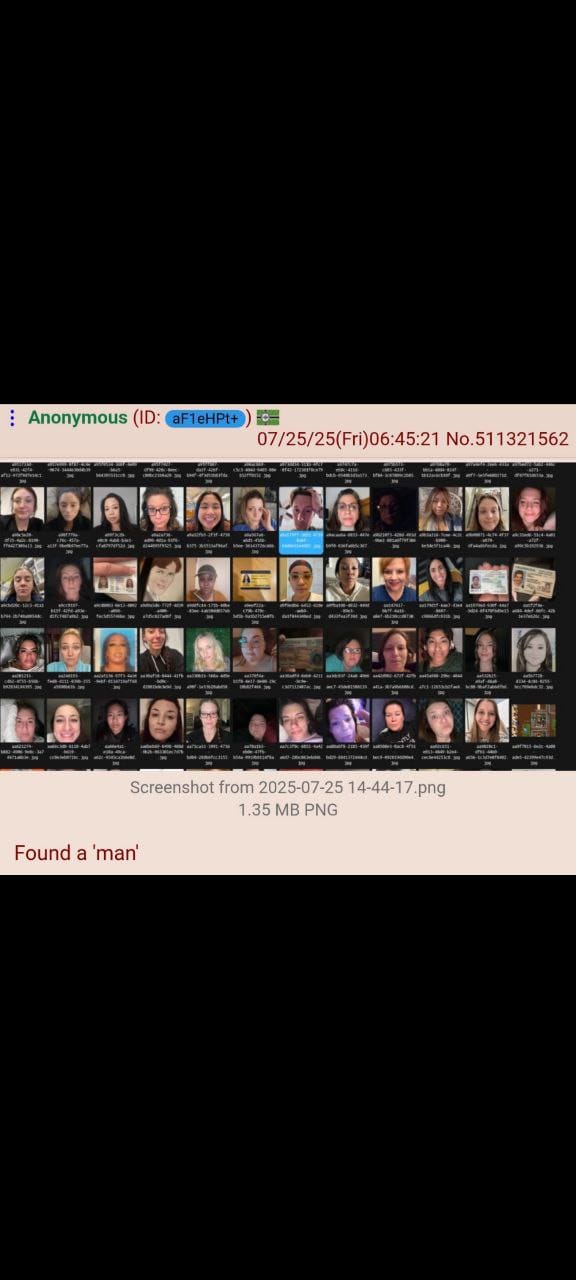
Scale of the Breach
The exposed data included:
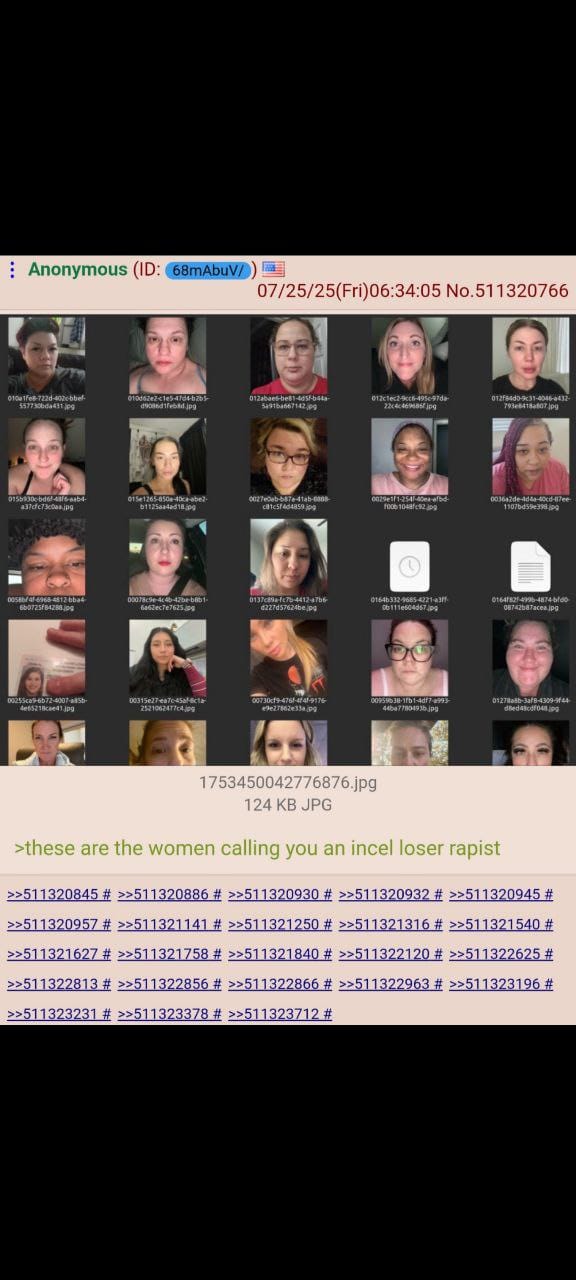
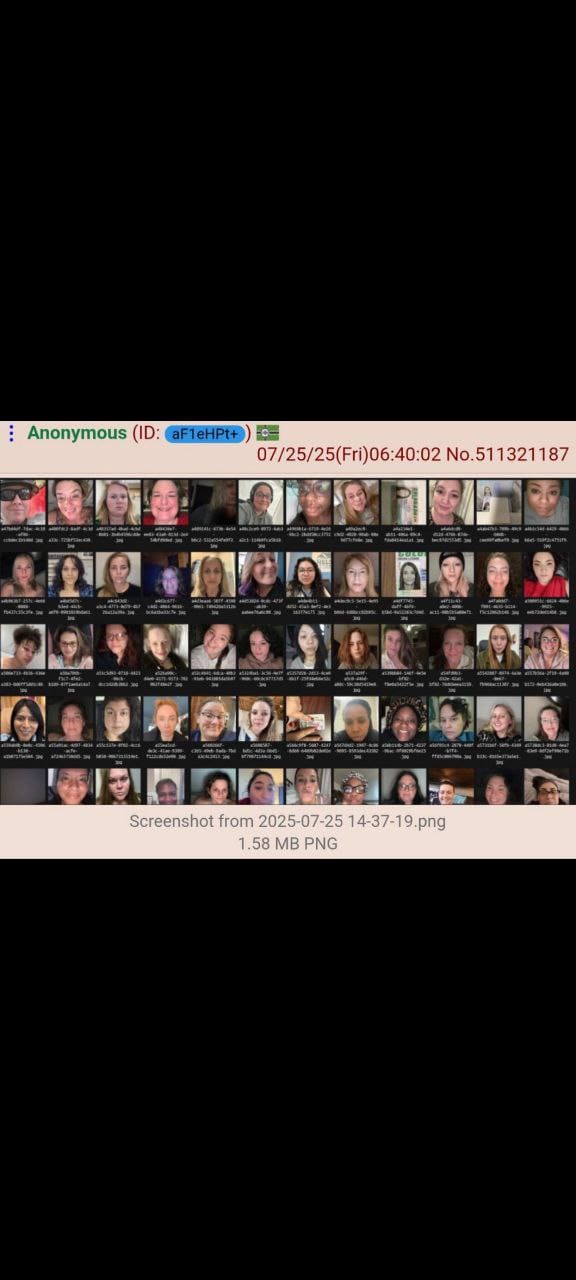
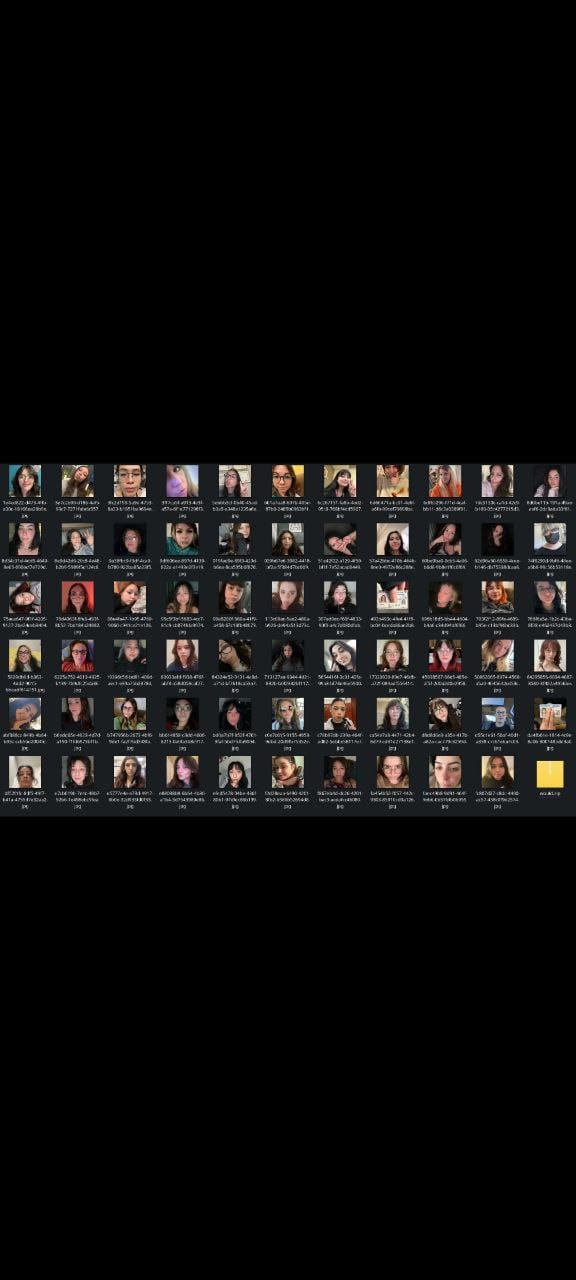
- 72,000+ user verification photos including selfies and driver's licenses
- Personal identification documents with full names, addresses, and dates of birth
- Some direct messages between users
- Location data tied to user profiles
4chan users created automated scripts to mass-download the exposed files, with some claiming to have collected thousands of women's personal documents within hours of the discovery.
Company Response Falls Short
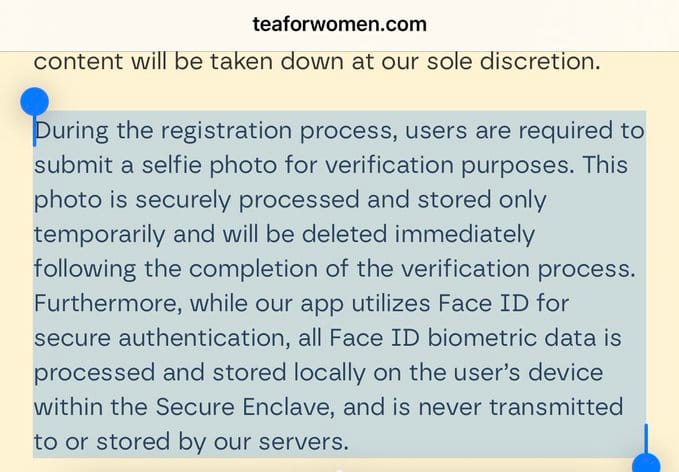
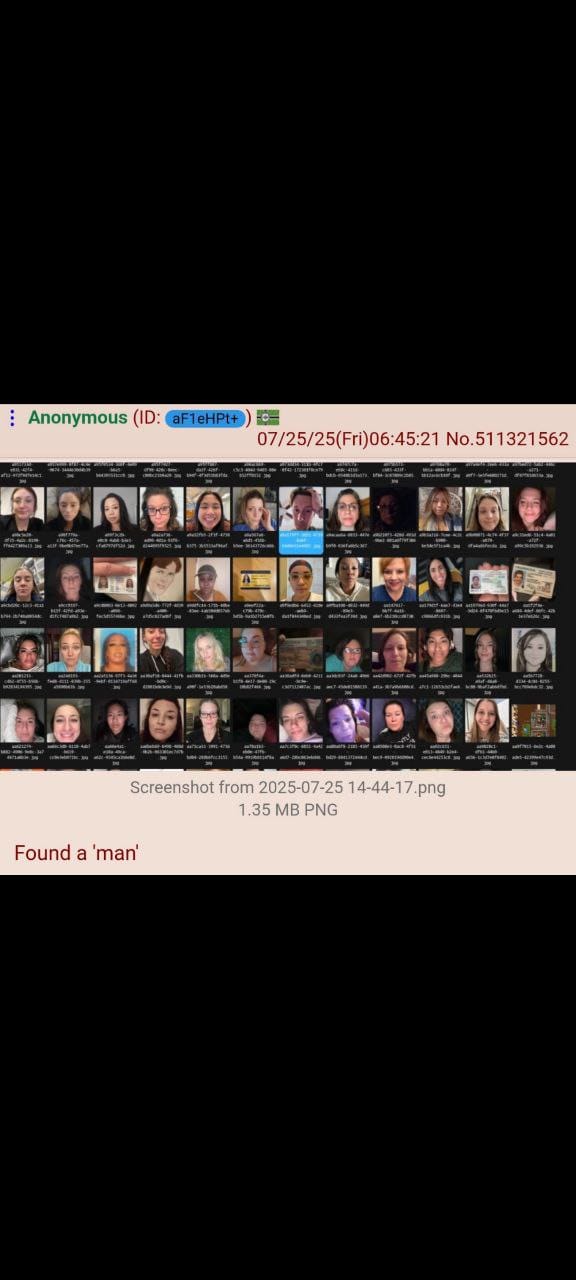
Tea's response to the breach has been inadequate and contradictory. The company initially claimed the exposed data was "from more than two years ago" and that "no current user data is affected."
This explanation raises serious questions, as the app only went viral and gained massive popularity this week. If the data is truly two years old, why was it still accessible? And why were recent users' verification photos apparently included in the leak?
The company's founder, Sean Cook, has not responded to media requests for comment, leaving users in the dark about the full scope of the breach and what steps are being taken to protect them.


The Bigger Picture
This breach highlights the dangerous intersection of good intentions and poor execution. Tea's mission—helping women stay safe while dating—is admirable and addresses a real need. However, the app's complete failure to secure users' most sensitive personal information has potentially put thousands of women at greater risk.
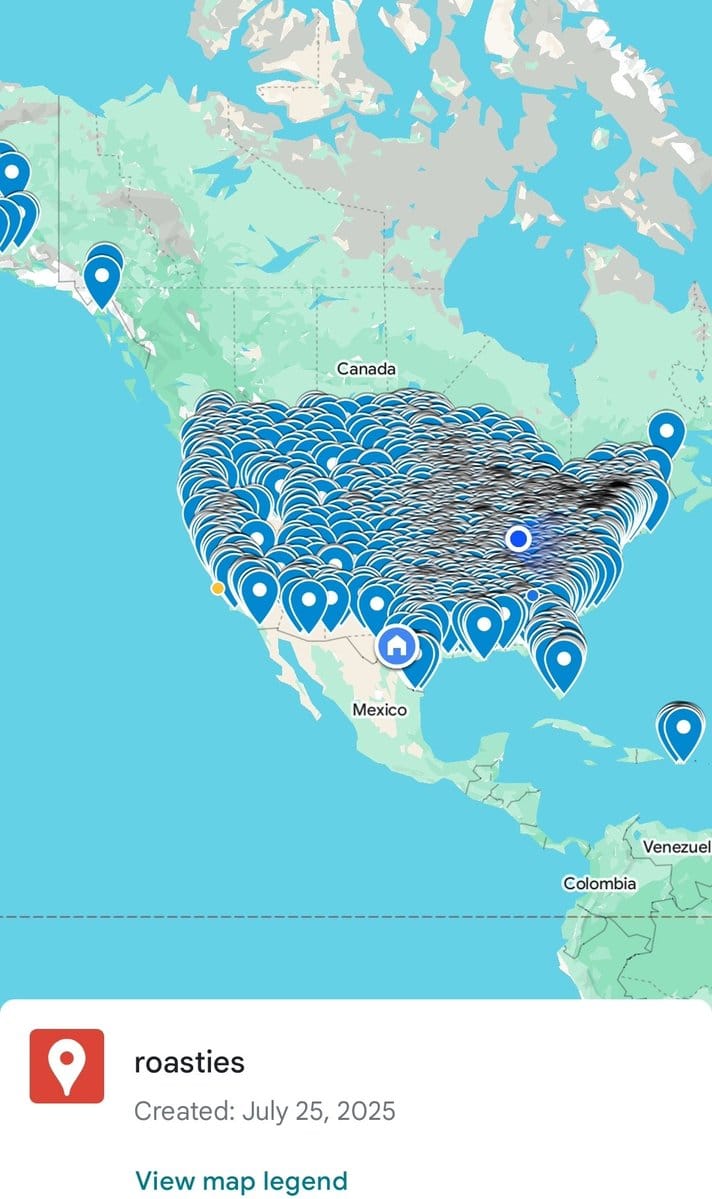
The irony is stark: an app designed to protect women's safety has become a tool that could facilitate stalking, harassment, or identity theft. The very women who trusted Tea with their most personal information to stay safe while dating now face the possibility of being doxxed by anonymous internet users.
Founder of Tea Dating Advice was a previously a product leader at Salesforce
— Jordi Hays (@jordihays) July 23, 2025
Massive moment for big tech PMs
Never doubt them again pic.twitter.com/UNoSsqcRIW
Rule Number Two: If you are the spouse of a high-ranking Congressman, don't take a selfie to sign up for a gossip app from inside the home of the individual you are having an affair with. https://t.co/Rljo37G8lD pic.twitter.com/YGViGLFSIl
— BelowTheTearline (@BelowTearline) July 25, 2025
What Users Should Do
If you've used the Tea app:
- Monitor your identity - Watch for signs of identity theft or unauthorized use of your personal information
- Consider a credit freeze - Protect yourself from potential financial fraud
- Document everything - Keep records of your Tea account and any suspicious activity
- Report incidents - Contact authorities if you experience harassment or stalking that may be linked to the breach
The Cost of Poor Security
This incident serves as a cautionary tale about the importance of cybersecurity, especially for apps handling sensitive personal data. Tea's decision to store unencrypted user verification documents in a public, unsecured database represents a fundamental failure of basic security practices.
For an app built around safety and trust, this breach may prove fatal to both its reputation and its mission. The women who needed Tea's protection the most are now the ones most at risk from its catastrophic security failures.
Someone created a website where you can rate the users of the hacked feminist doxing app "Tea".
— R. Augustine Sánchez 🏴☠️ (@ryanasanchez) July 26, 2025
Is this the most chopped userbase of all time? pic.twitter.com/0HwSxWCMnS
Tea's Competitors: How Do They Stack Up on Security?
The Tea app breach highlights a critical gap in the women's dating safety space. Here's how Tea's main competitors handle security and user protection:
Are We Dating The Same Guy (AWDTSG) Facebook Groups
The original inspiration for Tea came from the "Are We Dating The Same Guy?" Facebook groups, which have over 3.5 million members across 200+ individual groups worldwide. Unlike Tea's centralized app approach, AWDTSG operates through private Facebook groups where women share dating profiles and experiences.
Security differences:
- No identity verification required - Users only need a Facebook account
- Screenshots allowed - Unlike Tea's anti-screenshot technology, Facebook groups can't prevent image sharing
- Platform liability - Facebook's infrastructure handles data security, rather than a startup's potentially vulnerable systems
- Legal challenges - Multiple defamation lawsuits have been filed against AWDTSG groups, with one man in Los Angeles suing for $2.6 million
Noonlight: America's #1 Safety App
Noonlight protects over 3 million users and is America's number one safety app, with integrated compatibility with Tinder and other major dating platforms. Unlike Tea's community-driven approach, Noonlight focuses on emergency response.
Key features:
- Emergency button technology - Users hold a button when feeling unsafe; releasing without entering a code alerts police
- Professional monitoring - 24/7 help centers with trained operators screen calls and connect users with appropriate emergency services
- Major platform integration - Match Group invested in Noonlight in 2020, integrating it across Tinder, Match, OkCupid, and other dating apps
- No personal review system - Focuses purely on emergency response rather than crowdsourced information sharing
Other Dating Safety Apps
Kitestring: A text-based check-in service that doesn't require app downloads - users set timers and receive SMS check-ins, with emergency contacts alerted if they don't respond
Arlo Safe: Professional security monitoring with live, medically trained experts available 24/7
bSafe: Voice activation and live streaming capabilities for emergency situations
The Security Comparison
What makes Tea's breach particularly damaging is how it contrasts with its competitors:
- AWDTSG groups rely on Facebook's established infrastructure rather than building their own vulnerable systems
- Noonlight partners with major tech companies like Match Group, likely ensuring enterprise-level security standards
- Traditional safety apps focus on emergency response rather than storing sensitive identity documents
Tea's approach of requiring driver's licenses and ID verification created a honeypot of sensitive personal data that proved irresistible to malicious actors. In contrast, most competitors either avoid collecting such sensitive information or rely on established platforms with proven security track records.
The lesson is clear: good intentions in women's safety technology mean nothing without proper cybersecurity infrastructure to protect the very users you're trying to help.
This story is developing as more details about the breach continue to emerge.





