The Complete Guide to OSINT Protection: Defend Against Open Source Intelligence Gathering in 2025
In the digital age, your personal information is scattered across thousands of publicly accessible databases, social media profiles, government records, and commercial websites. What most people don't realize is how easily this seemingly harmless information can be weaponized against them through Open Source Intelligence (OSINT) techniques—sophisticated methods that can reveal shocking details about your life, habits, relationships, and vulnerabilities without ever requiring illegal access to your private accounts.
OSINT practitioners can discover where you live, work, and travel. They can identify your family members, financial status, political views, and personal routines. They can predict your behavior, exploit your relationships, and in some cases, even access your physical location in real-time. This isn't science fiction—it's happening right now to millions of people who have no idea they're being systematically profiled using information they voluntarily made public.
The challenge isn't just the sophistication of modern OSINT tools—it's that most people have no concept of their digital exposure level or how to defend against intelligence gathering techniques. Traditional privacy advice focuses on securing accounts and devices while ignoring the massive information trail everyone leaves through public records, social media activity, and commercial data collection.
This comprehensive guide reveals how OSINT techniques work, what information they can discover about you, and most importantly, how to implement effective countermeasures that dramatically reduce your exposure to intelligence gathering while maintaining your digital lifestyle.
Understanding the OSINT Threat Landscape
Open Source Intelligence gathering has evolved from a specialized military and intelligence discipline into a democratized practice accessible to anyone with internet access and basic research skills. The same techniques once reserved for government agencies are now used by private investigators, corporate security teams, criminals, stalkers, and curious individuals who want to learn more about specific targets.
What makes OSINT particularly dangerous is its legal and ethical gray area. All the information gathered comes from publicly available sources, making the practice generally legal while remaining highly invasive. This creates a perfect storm where sophisticated intelligence gathering operates with minimal oversight or protection for targets.
Modern OSINT practitioners don't just search Google and social media—they use specialized tools, databases, and techniques that can correlate information across hundreds of sources to build comprehensive profiles that reveal far more than any individual source would suggest.
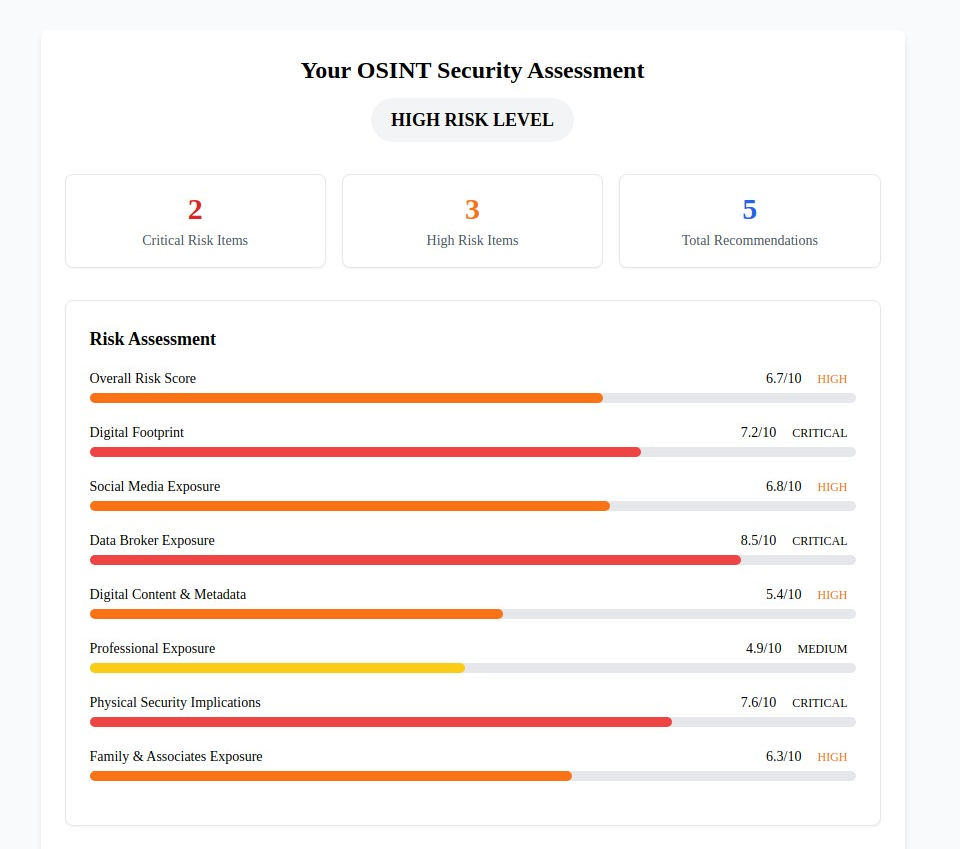
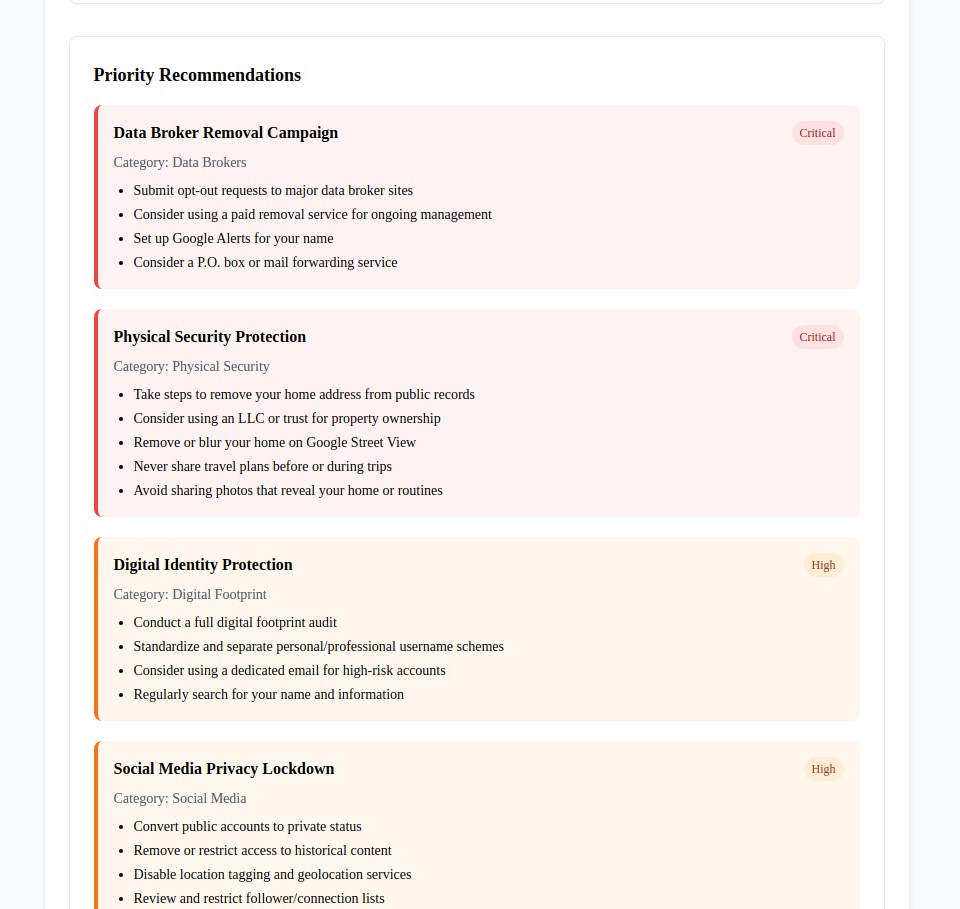
Discover your OSINT exposure level with our comprehensive OSINT Security Self-Assessment. This specialized evaluation analyzes your vulnerability across eight critical categories and provides personalized recommendations to reduce your intelligence gathering exposure.
The Eight Critical OSINT Exposure Categories
Our analysis of thousands of OSINT investigations reveals that comprehensive intelligence gathering exploits vulnerabilities across eight interconnected categories. Understanding these categories is essential for effective protection:
Digital Information Sources:
- Digital Footprint Overview - Your overall online presence and information discoverability
- Social Media Exposure - How your social platforms reveal personal information and behavioral patterns
- Data Broker Presence - Your information's availability through commercial data aggregation services
- Digital Content & Metadata - Hidden information in photos, documents, and online content






